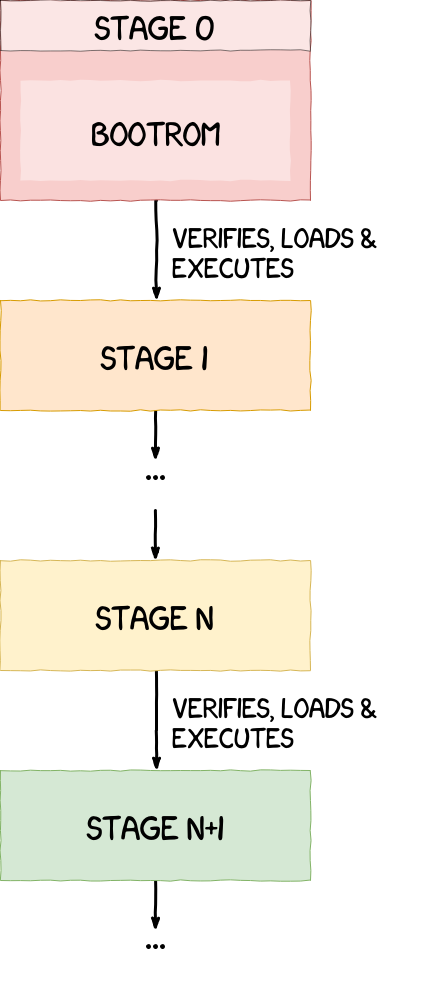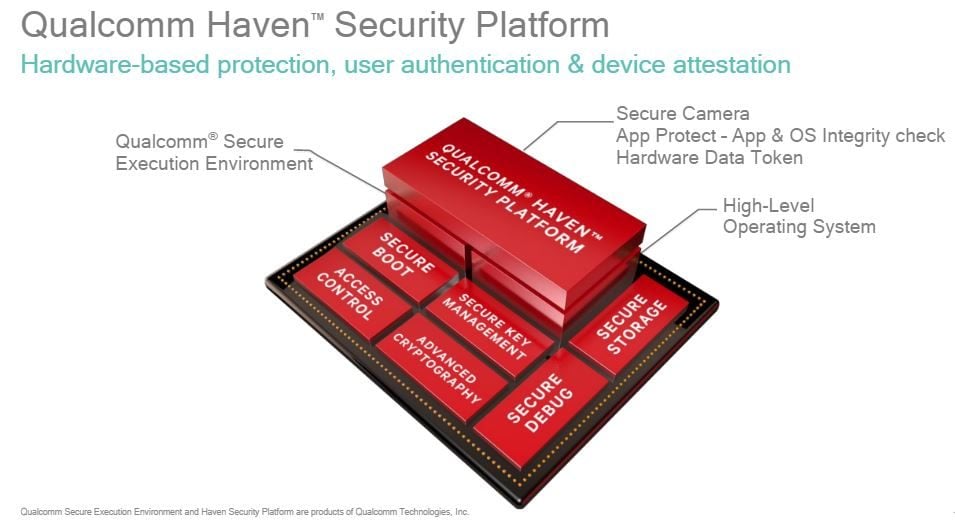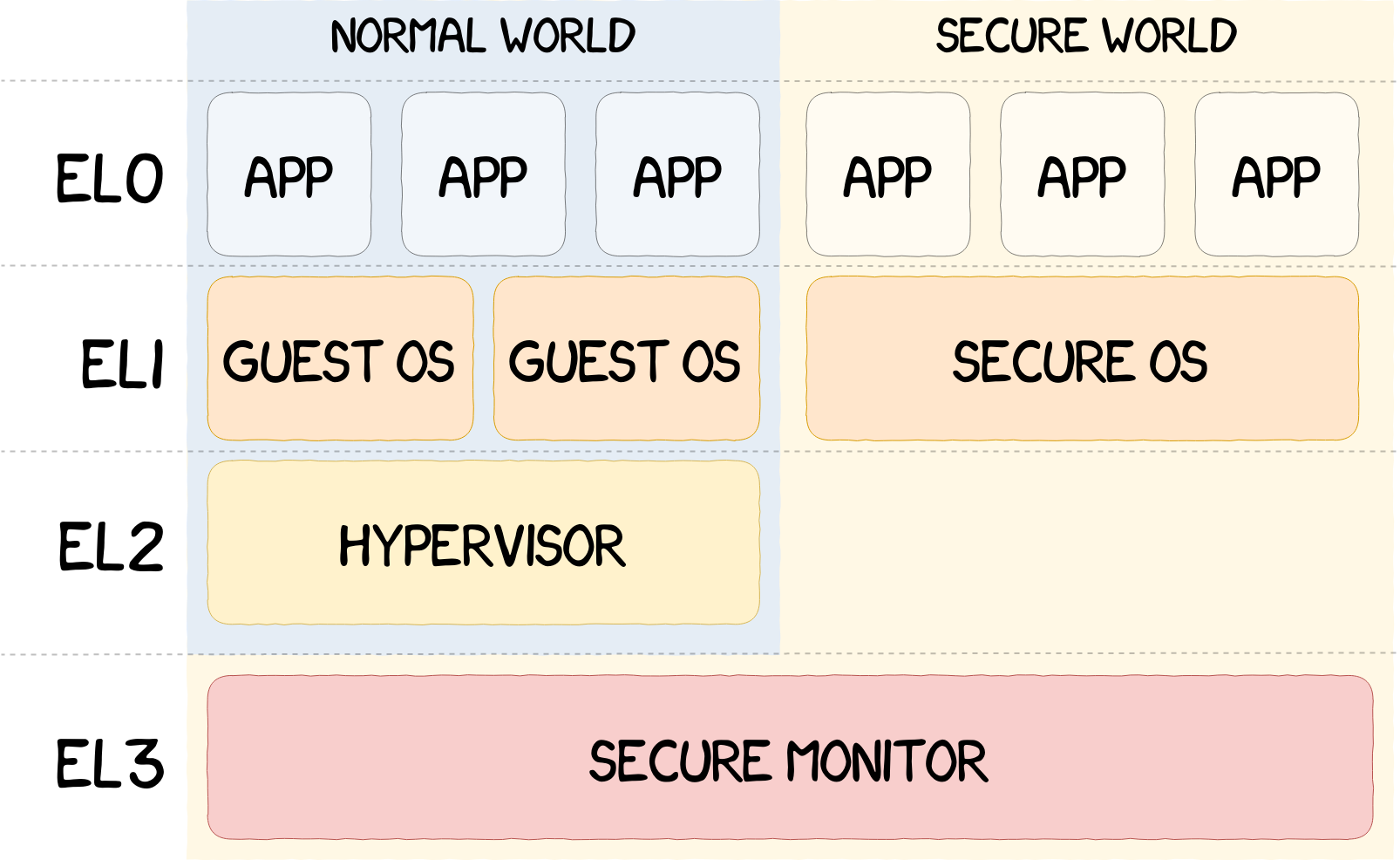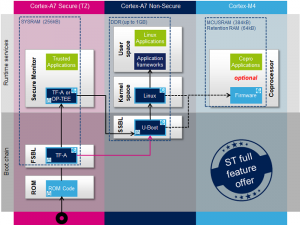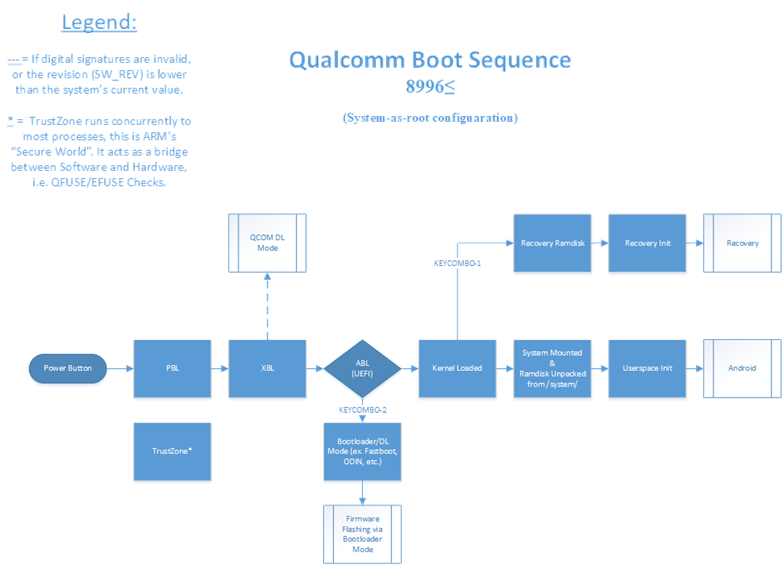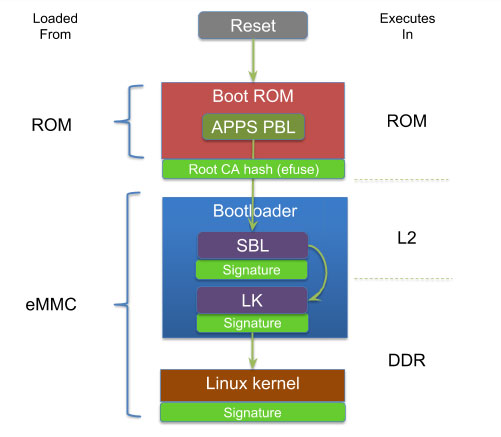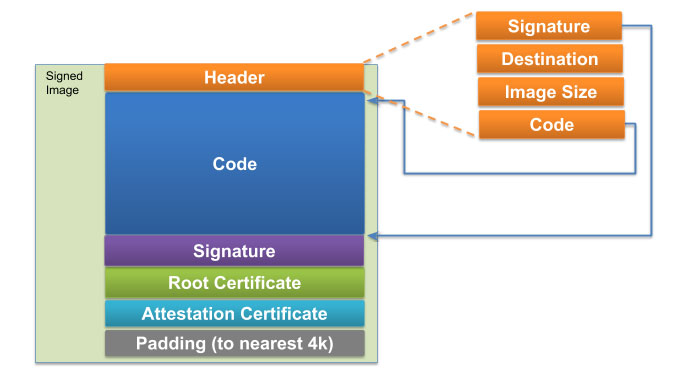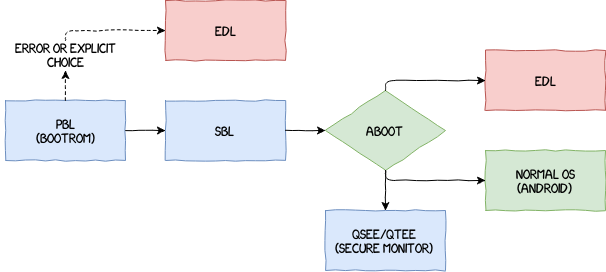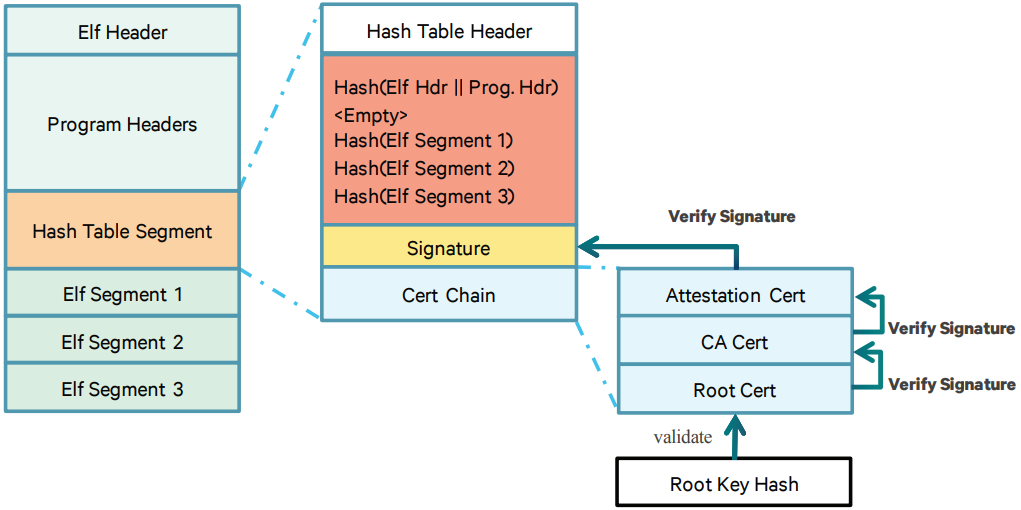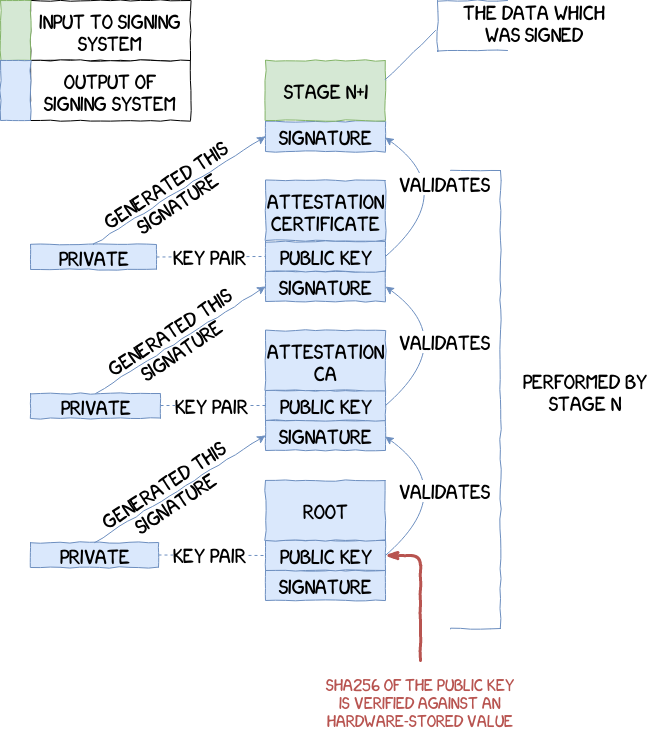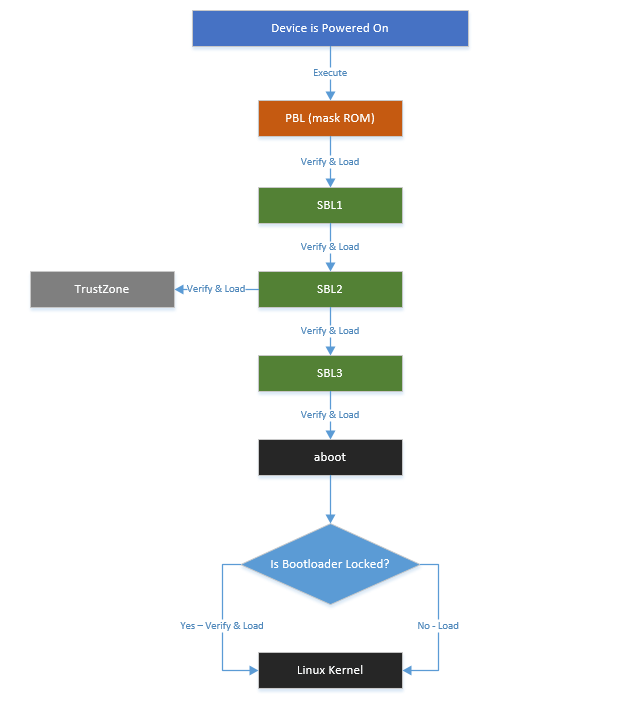
Qualcomm BL Signature Vulnerability: Android Secure Boot Mechanism Analysis and Bypass Testing – 1024研究所

android - What are the factors that effects the kernel build(Image) to flash on the device? - Stack Overflow
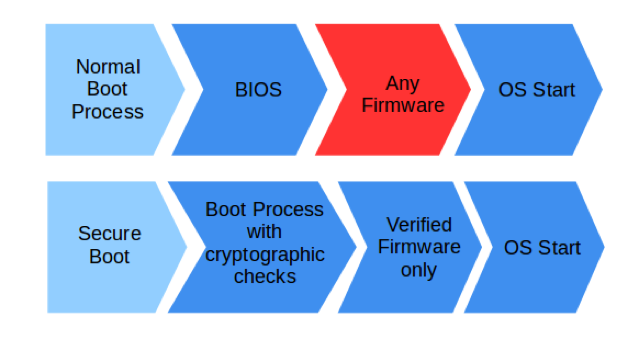
Signing, Building and Flashing an Image for Secure Boot on the Qualcomm® QCA4020/4024 Platform - Qualcomm Developer Network