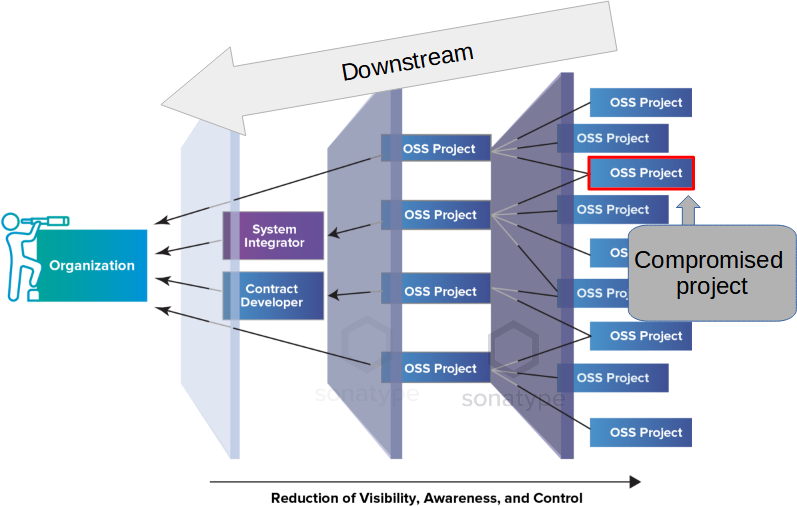
One in five data breaches due to software supply chain compromise, IBM report warns | The Daily Swig
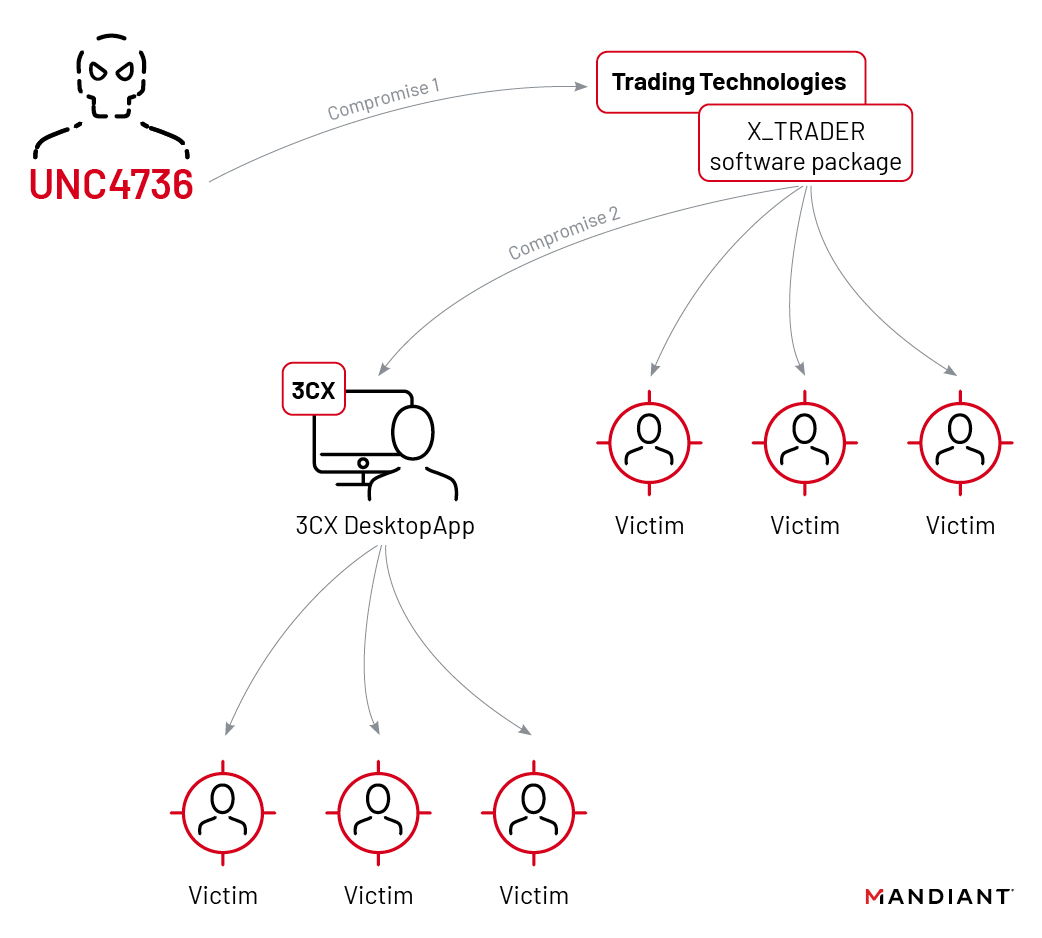
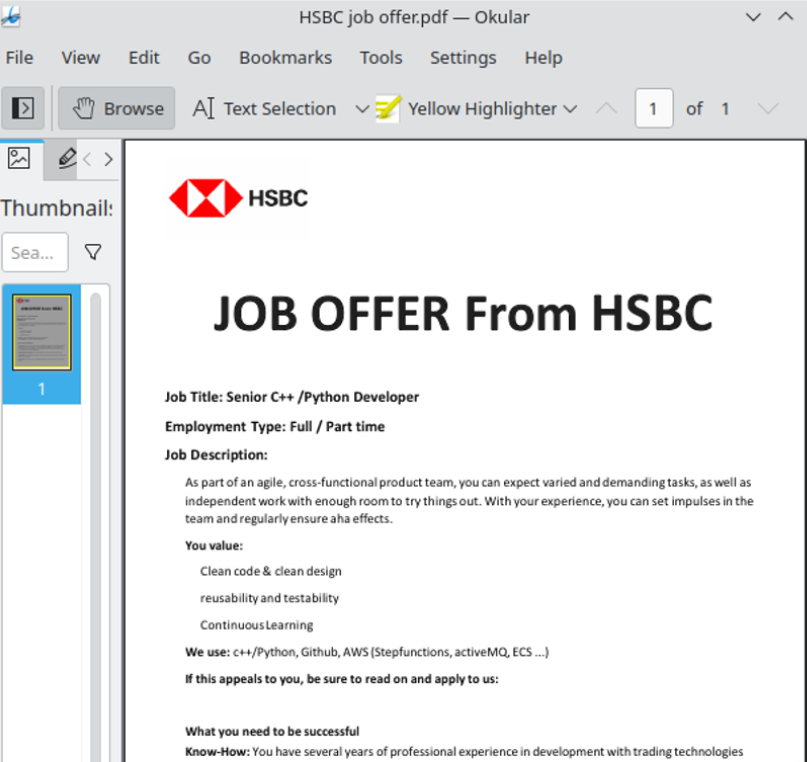
3CX Software Supply Chain Compromise Initiated by a Prior Software Supply Chain Compromise; Suspected North Korean Actor Responsible | Mandiant