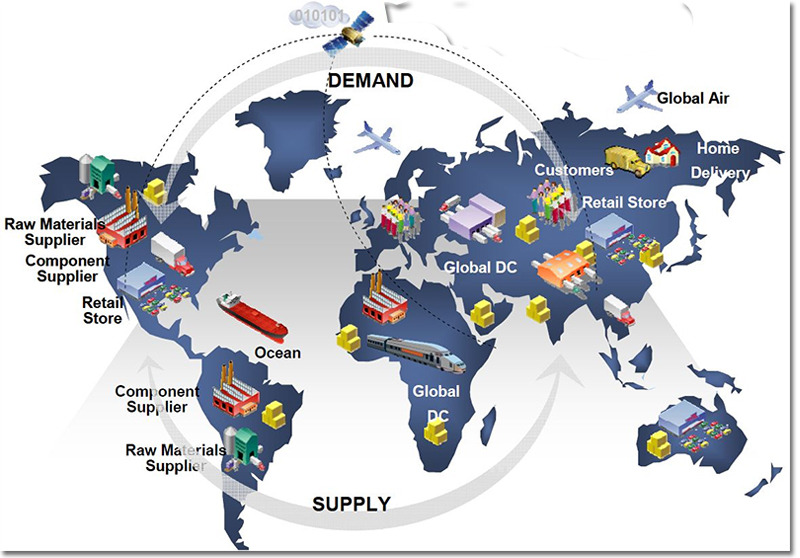
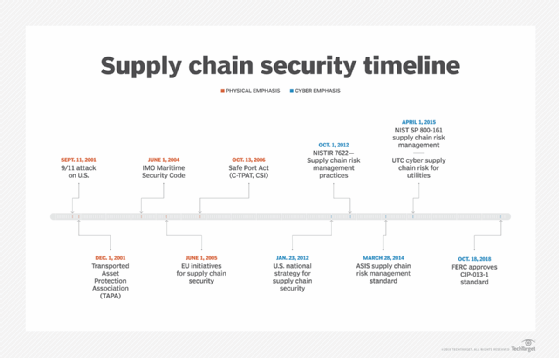
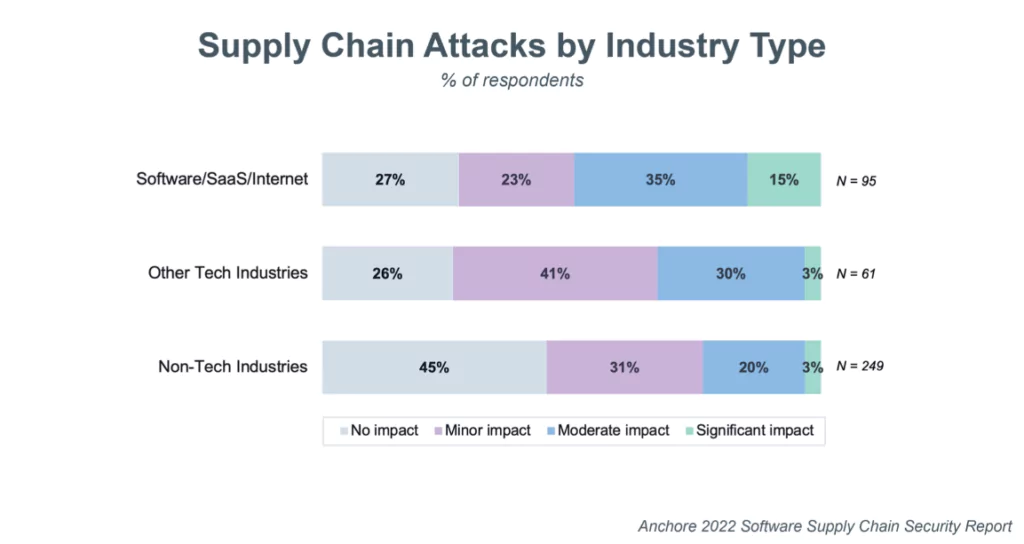
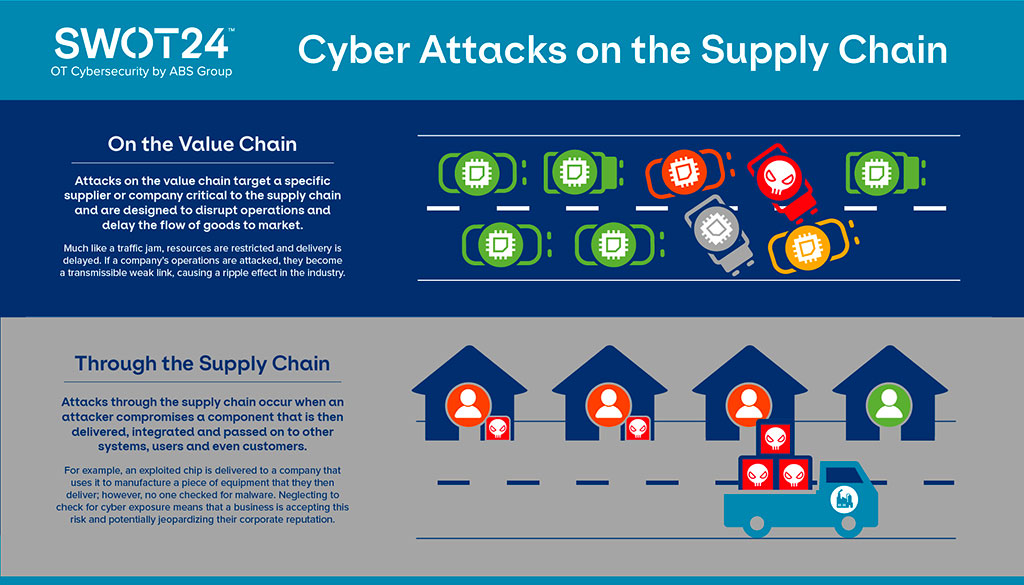
Understanding The Impact Cyber Threats Have On Supply Chains | Reuters Events | Supply Chain & Logistics Business Intelligence
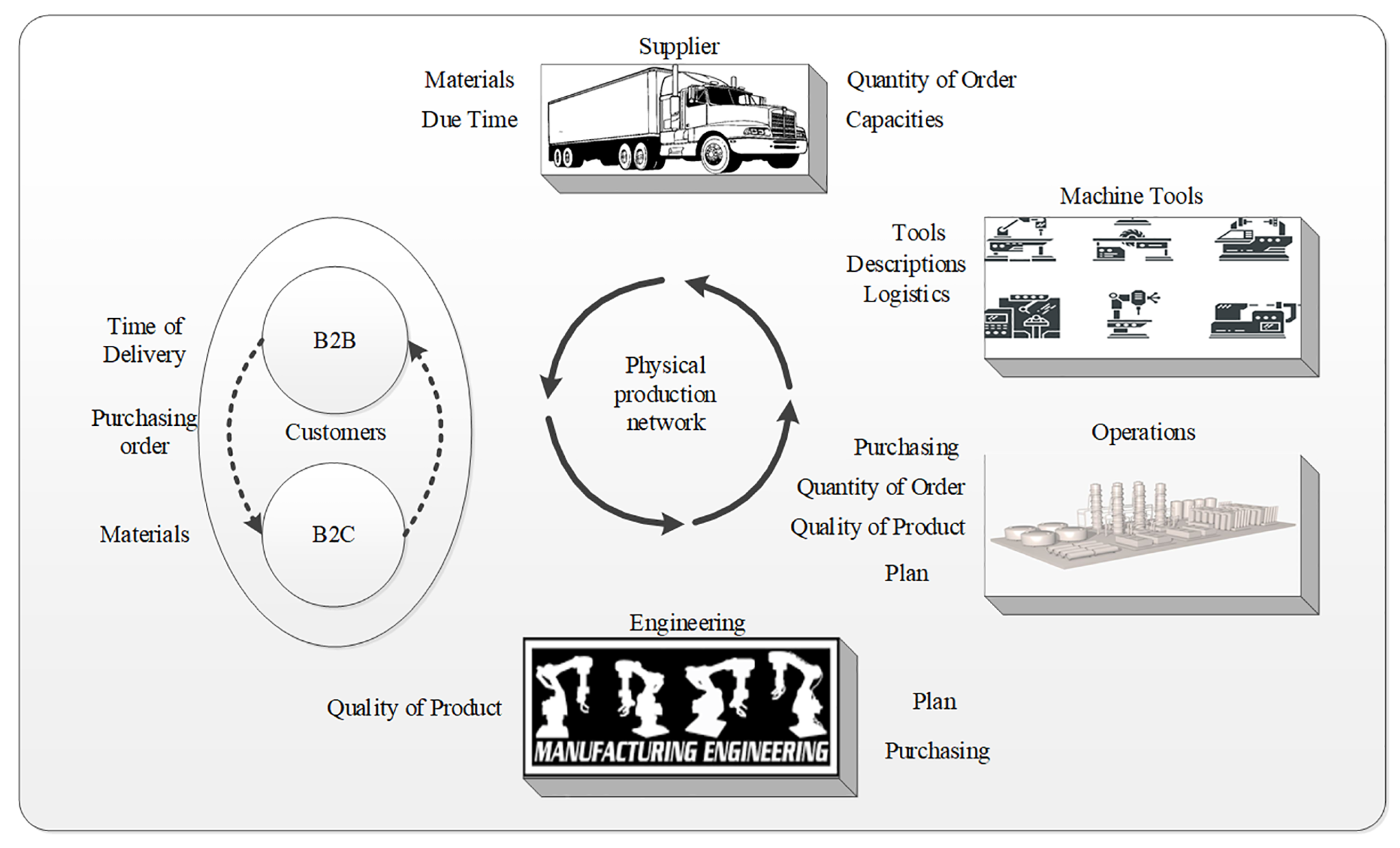
Electronics | Free Full-Text | Supply Chain 4.0: A Survey of Cyber Security Challenges, Solutions and Future Directions