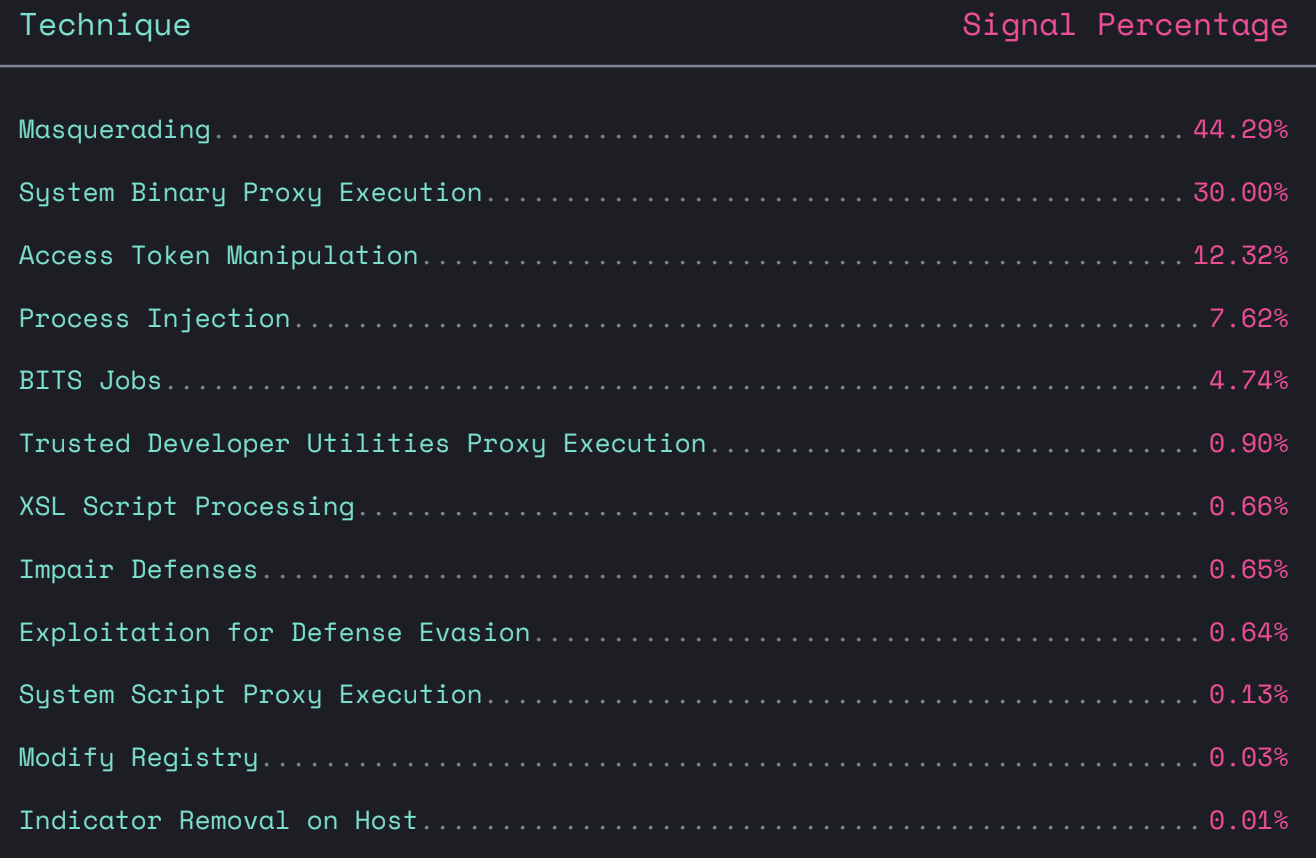
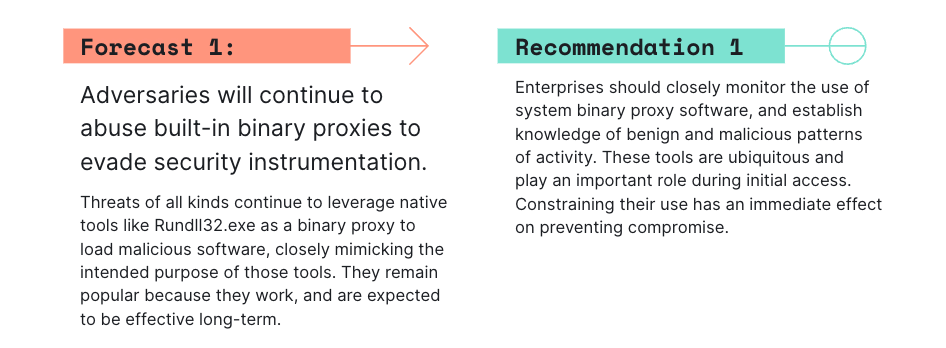
![Dec 8th, 2022: [EN] What you need to know: Elastic Global Threat Report 2022 - Advent Calendar - Discuss the Elastic Stack Dec 8th, 2022: [EN] What you need to know: Elastic Global Threat Report 2022 - Advent Calendar - Discuss the Elastic Stack](https://global.discourse-cdn.com/elastic/original/3X/c/8/c8ea3ef21617ac45d471acb0580bde440b09574b.jpeg)
Dec 8th, 2022: [EN] What you need to know: Elastic Global Threat Report 2022 - Advent Calendar - Discuss the Elastic Stack

Threat Hunting with Elastic Stack: Solve complex security challenges with integrated prevention, detection, and response: 9781801073783: Computer Science Books @ Amazon.com

Elastic Global Threat Report Reveals Nearly 33% of Cyberattacks in the Cloud Leverage Credential Access | Business Wire

Elastic Global Threat Report Reveals Nearly 33% of Cyberattacks in the Cloud Leverage Credential Access

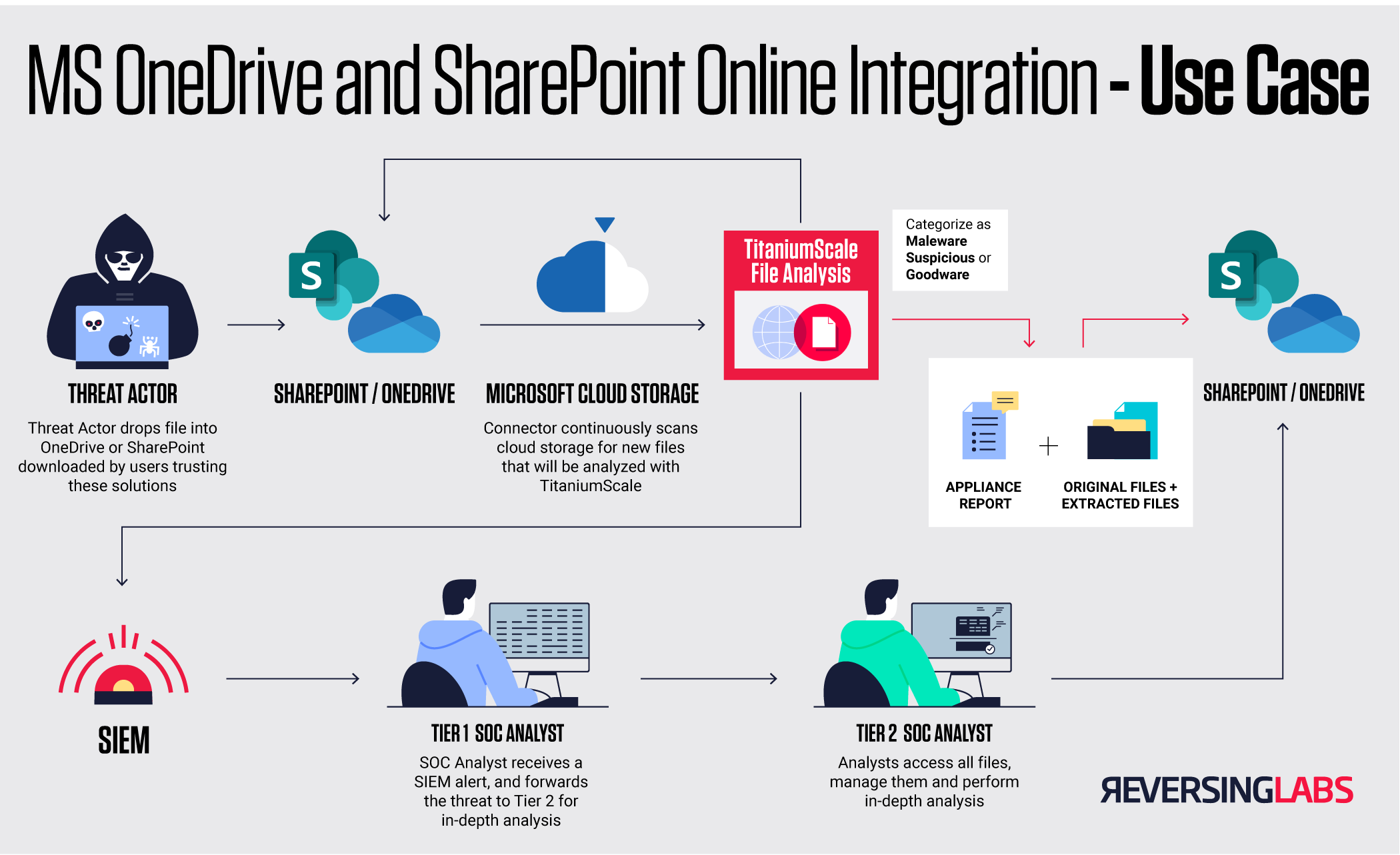

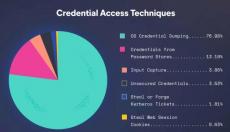








.png)