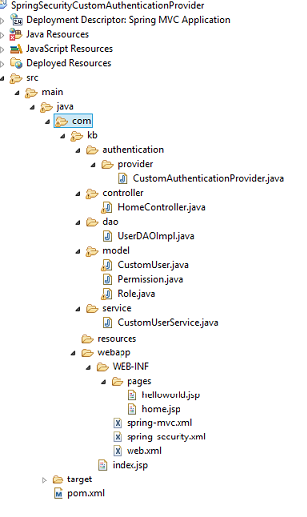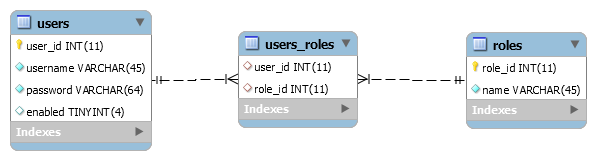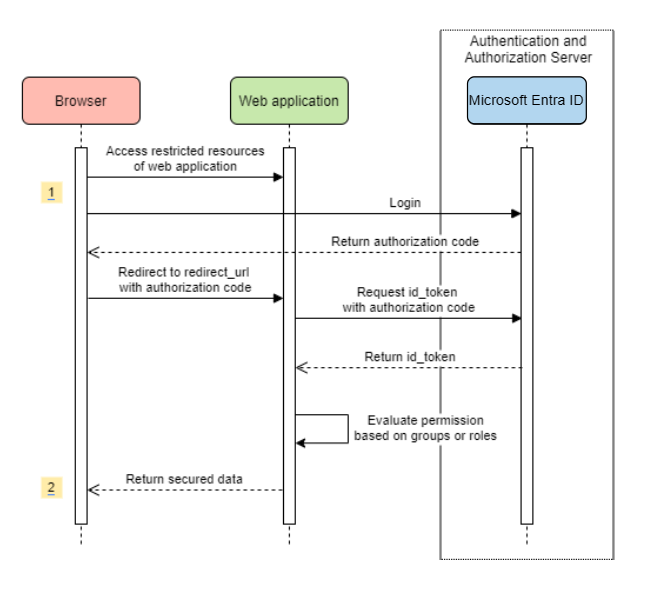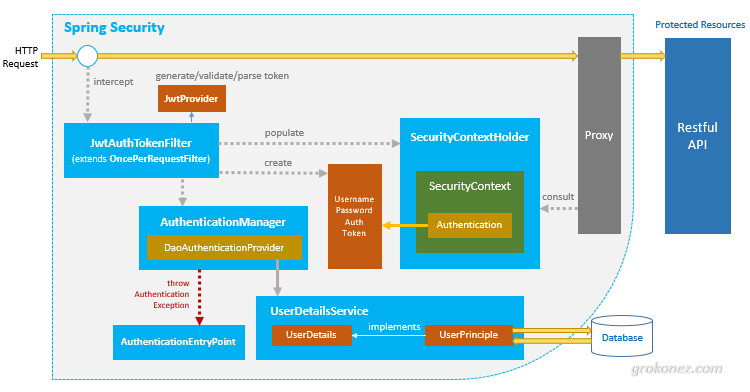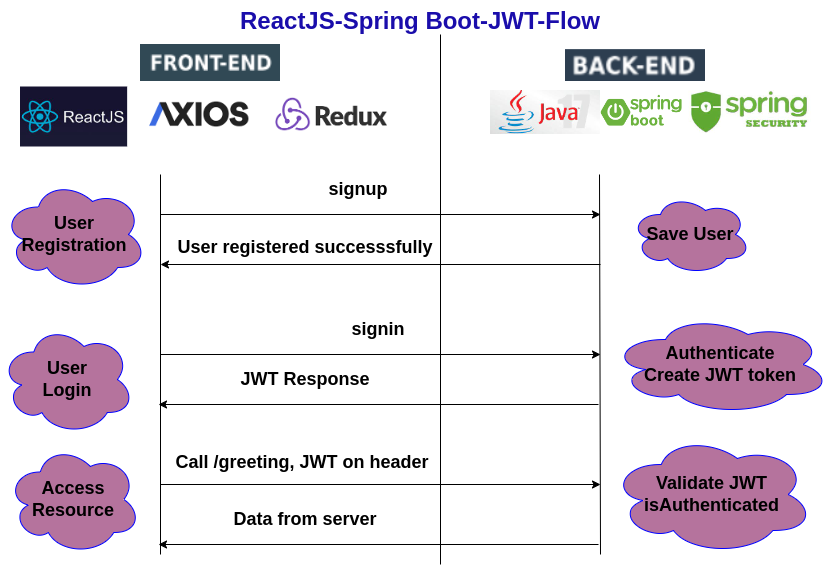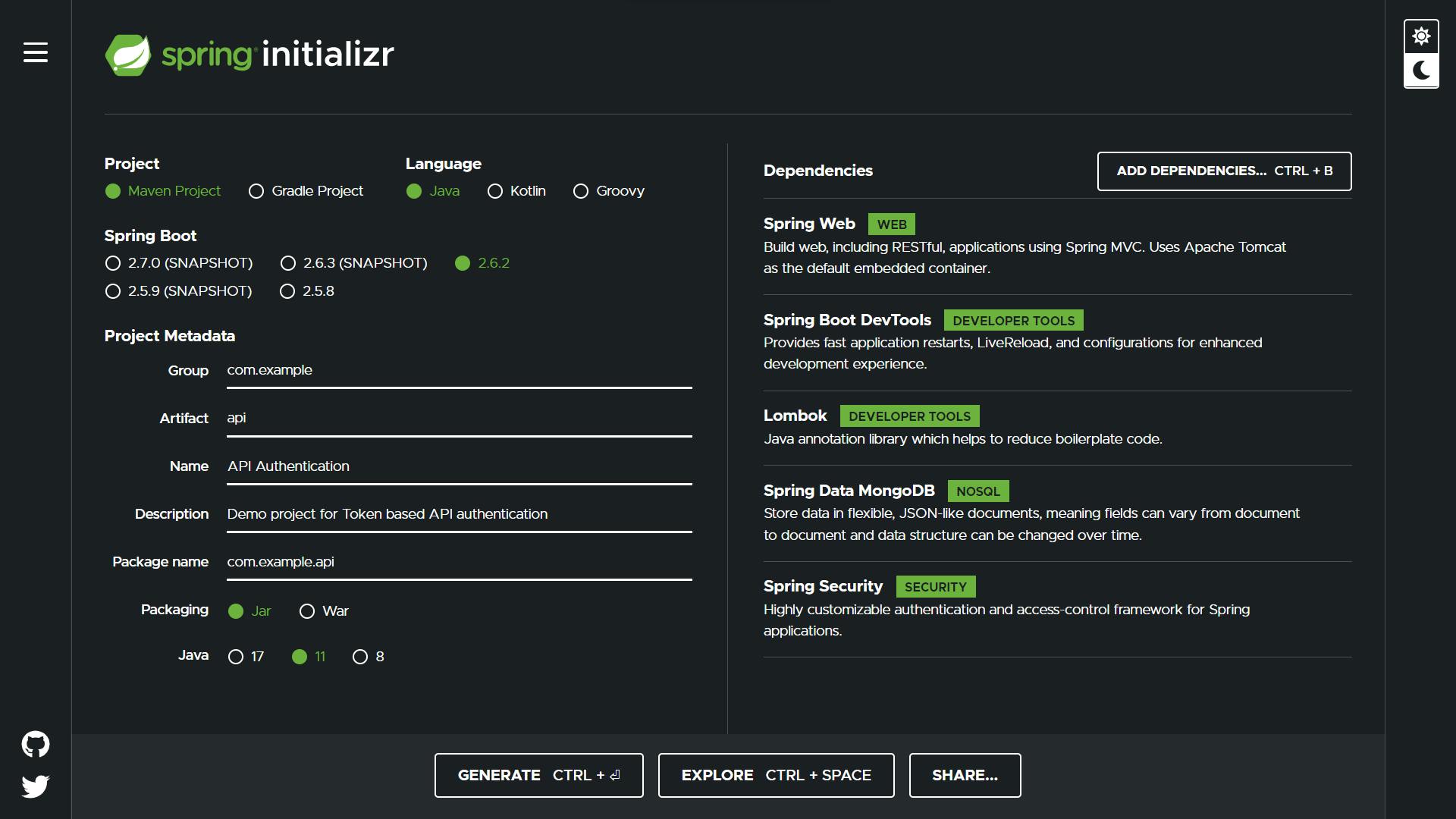
Spring Boot + Spring Security with JPA authentication and MySQL from scratch - Java Brains - YouTube
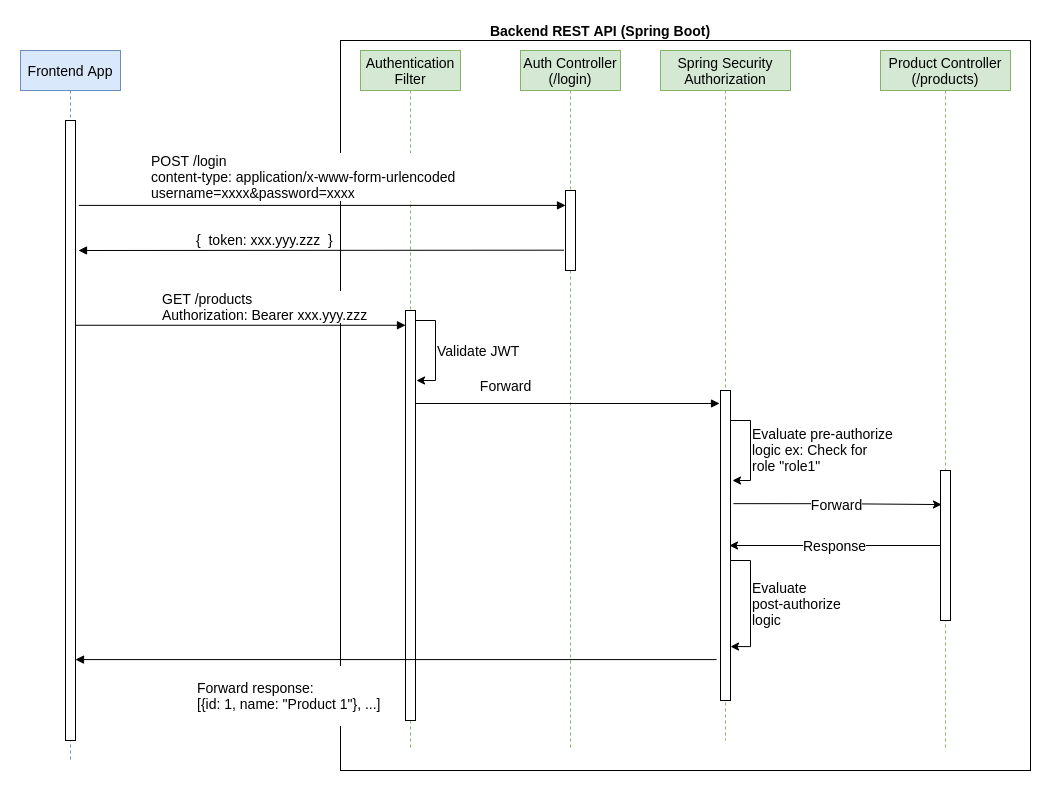
Role Based Access Control (RBAC) with Spring Boot and JWT | by Imesha Sudasingha | Geek Culture | Medium

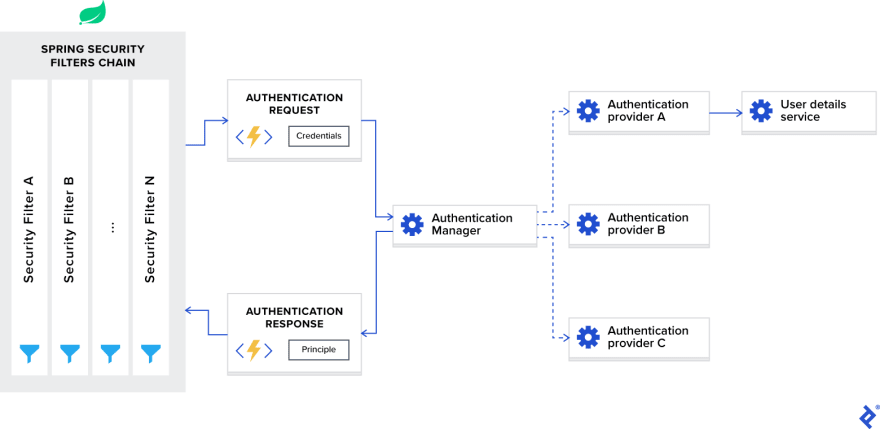
Spring Boot Security Configuration, practically explained – Part6: A deep intro to filter/token-based security - Panos Zafiropoulos - DevXperiences

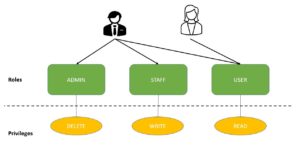
java - Implementation of Roles and Permissions in Spring Security - update: error related to hasPermission method - Stack Overflow