
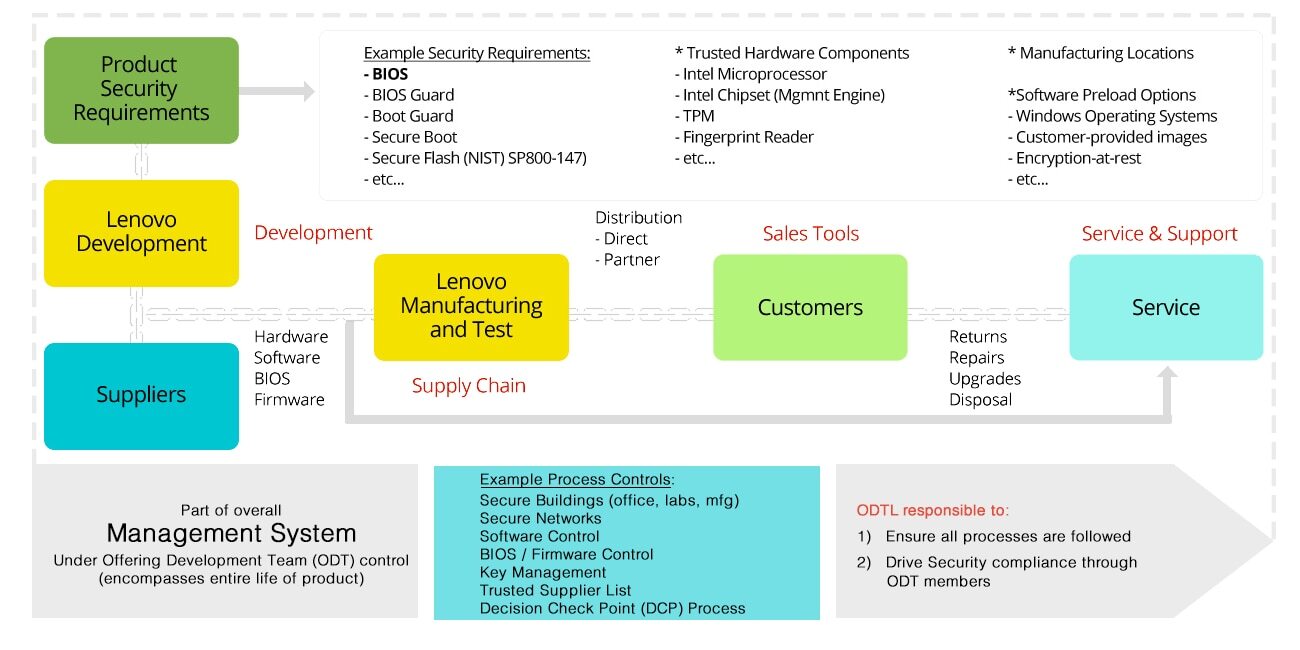
Addressing the hardware supply chain security challenge - Research Articles - Research Collaboration and Enablement - Arm Community

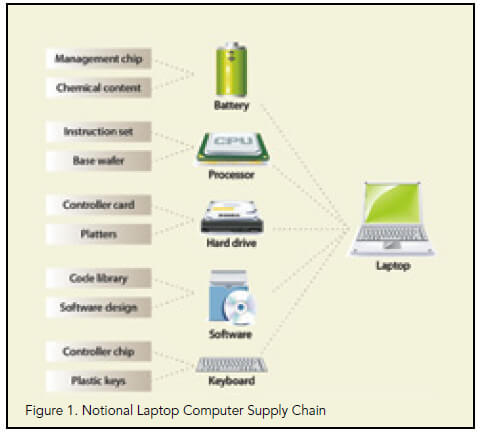
Hardware Supply Chain Security: Threat Modelling, Emerging Attacks and Countermeasures | SpringerLink

Hardware Supply Chain Security: Threat Modelling, Emerging Attacks and Countermeasures (English Edition) eBook : Halak, Basel: Amazon.fr: Boutique Kindle

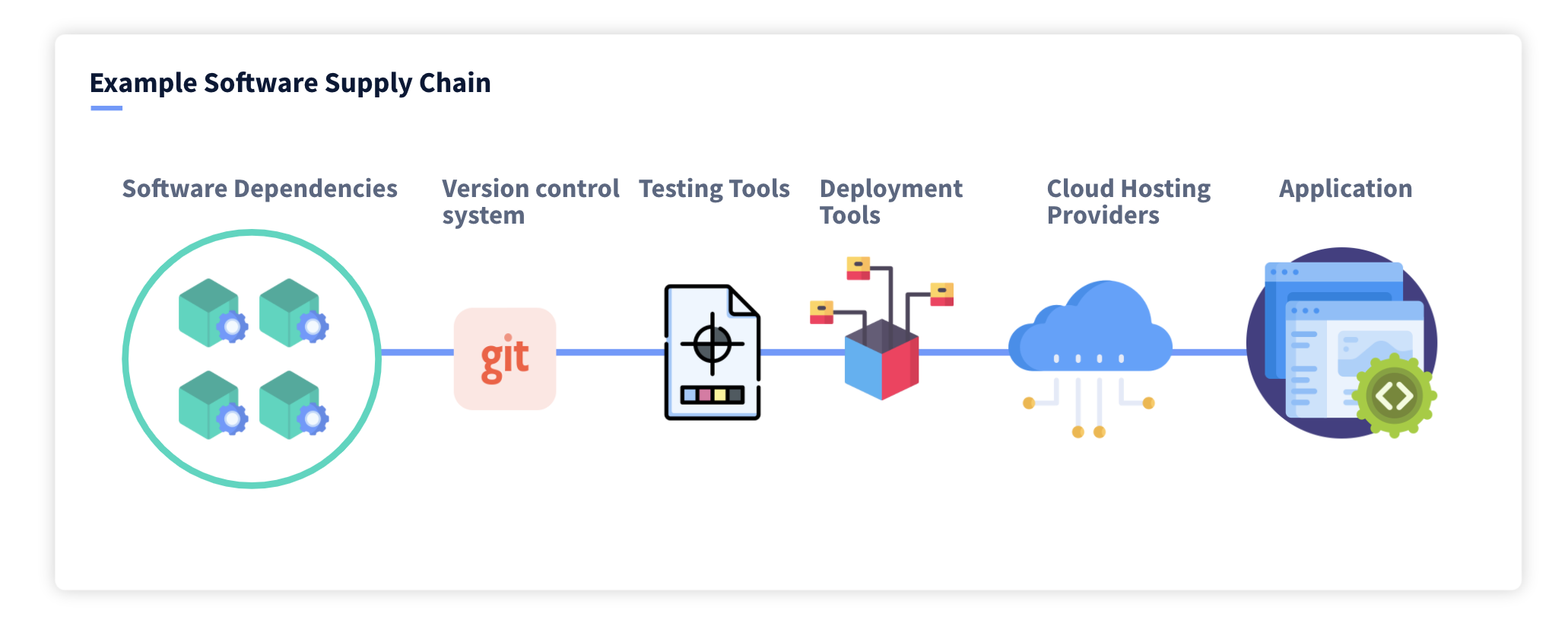
Relationship Between Security Concept and Security Assessment for Software Supply Chain - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.













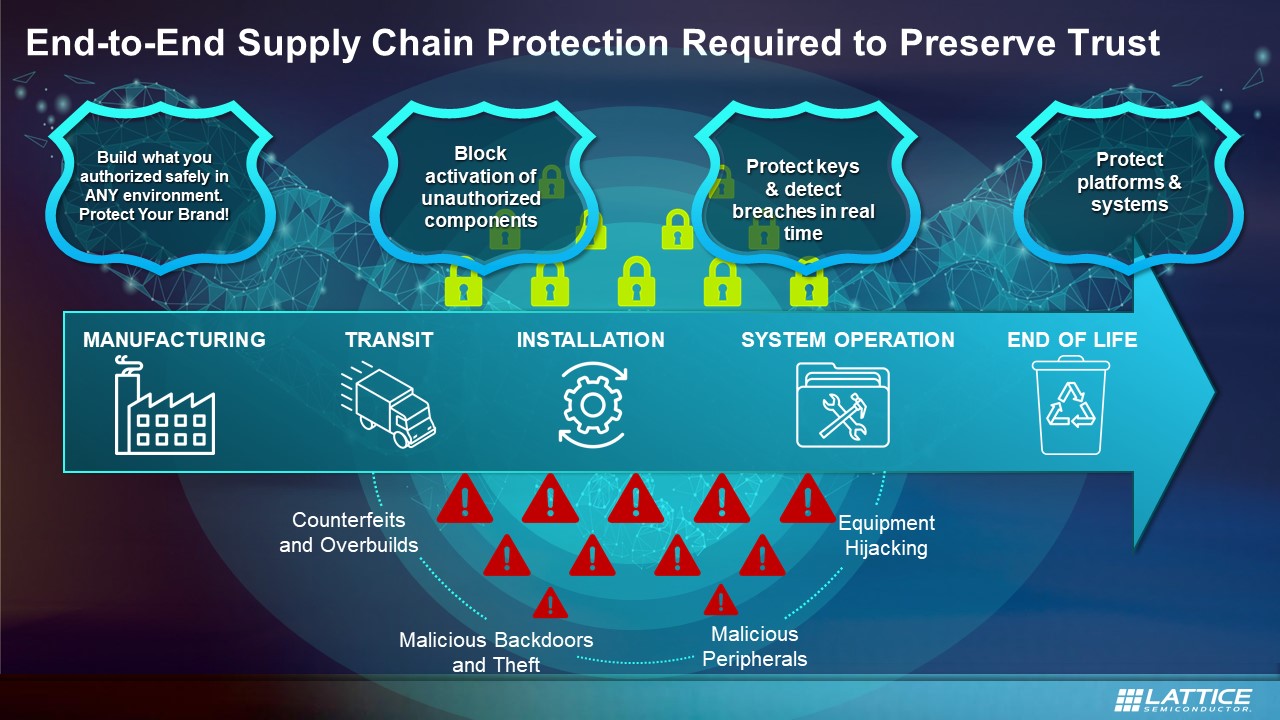
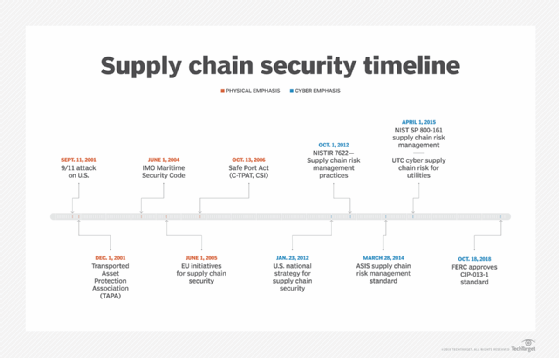
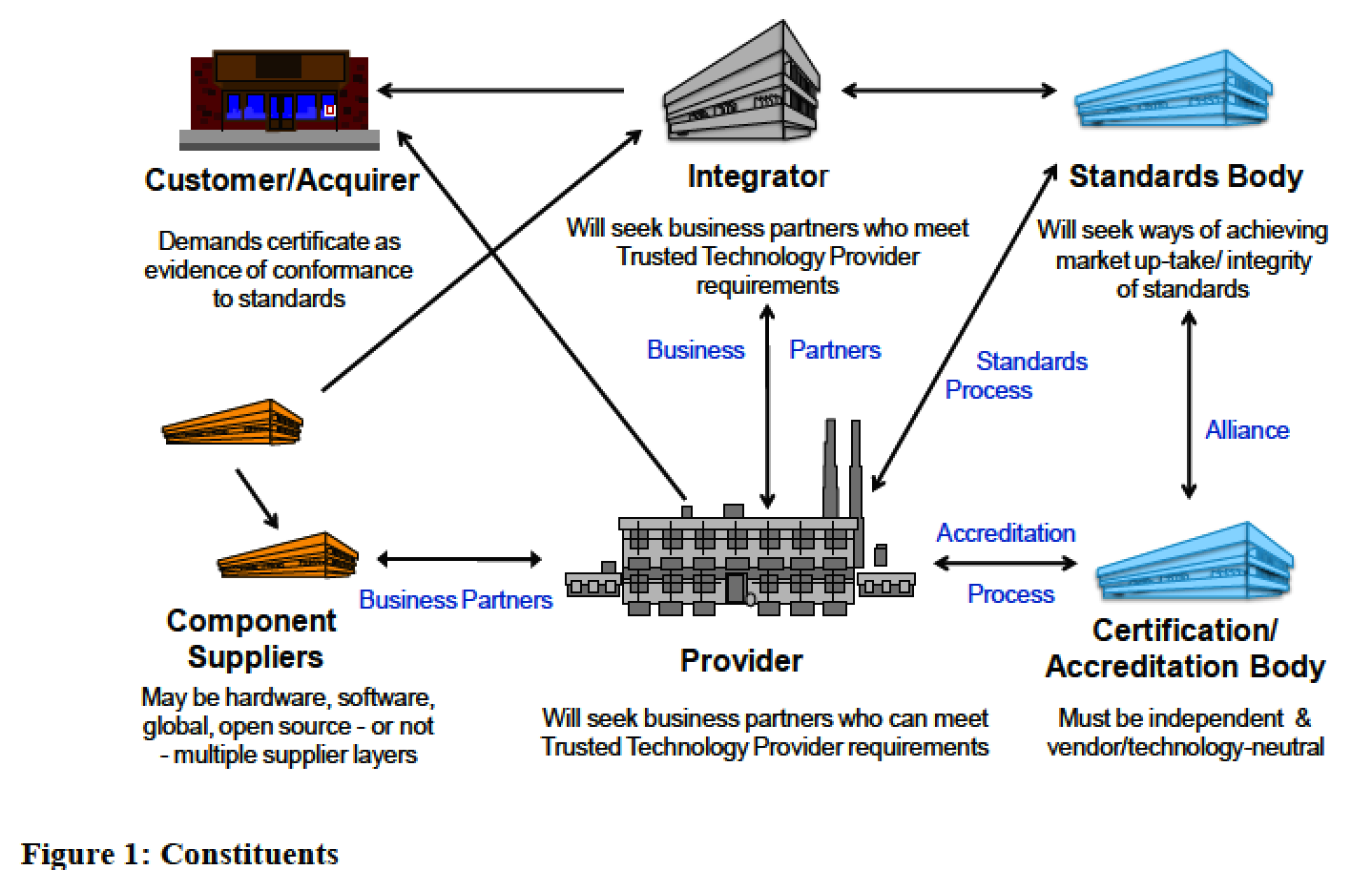

![Electronic supply chain security model [47]. | Download Scientific Diagram Electronic supply chain security model [47]. | Download Scientific Diagram](https://www.researchgate.net/publication/322221204/figure/fig1/AS:578552590082048@1514949094633/Electronic-supply-chain-security-model-47.png)