Securing the supply chain: Organizations need best practices in proactive security - Help Net Security
Range of potential NotPetya impacts on Maersk and its supply chain This... | Download Scientific Diagram

When the screens went black: How NotPetya taught Maersk to rely on resilience – not luck – to mitigate future cyber-attacks | The Daily Swig

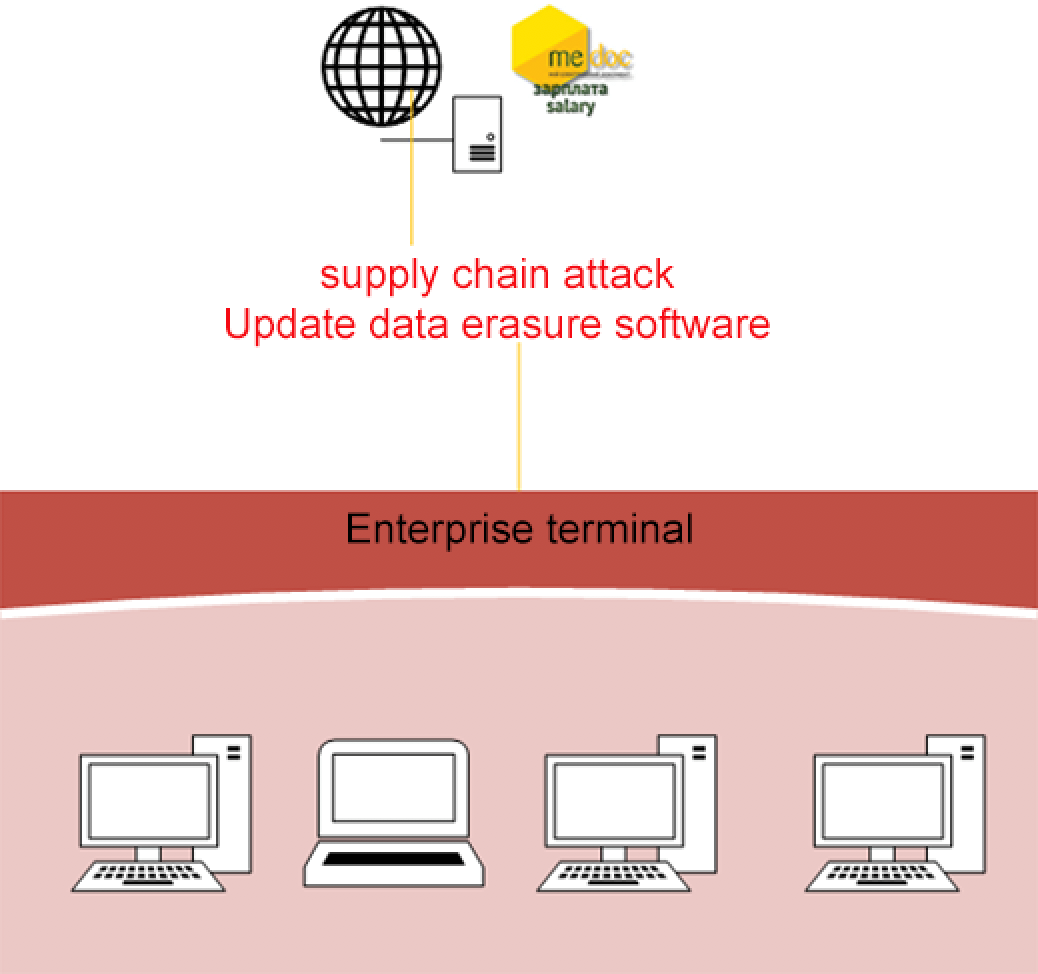
Throwback Attack: How NotPetya accidentally took down global shipping giant Maersk | Industrial Cybersecurity Pulse | Industrial Cybersecurity Pulse