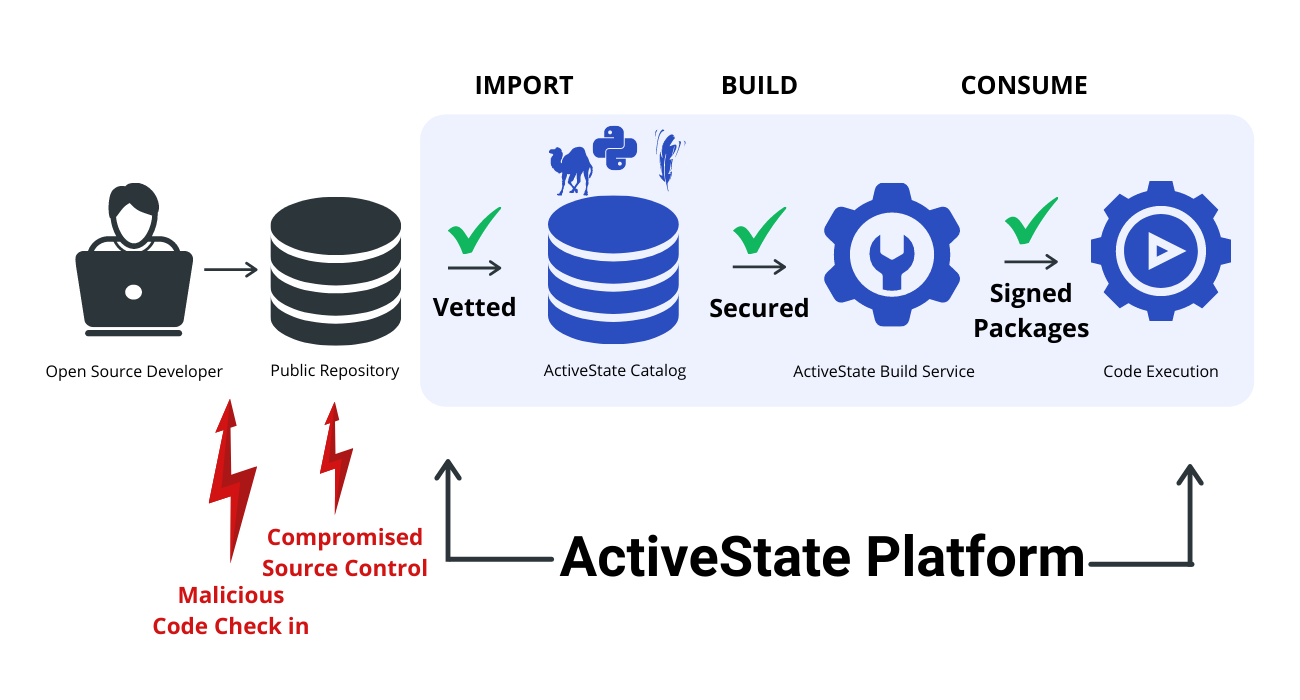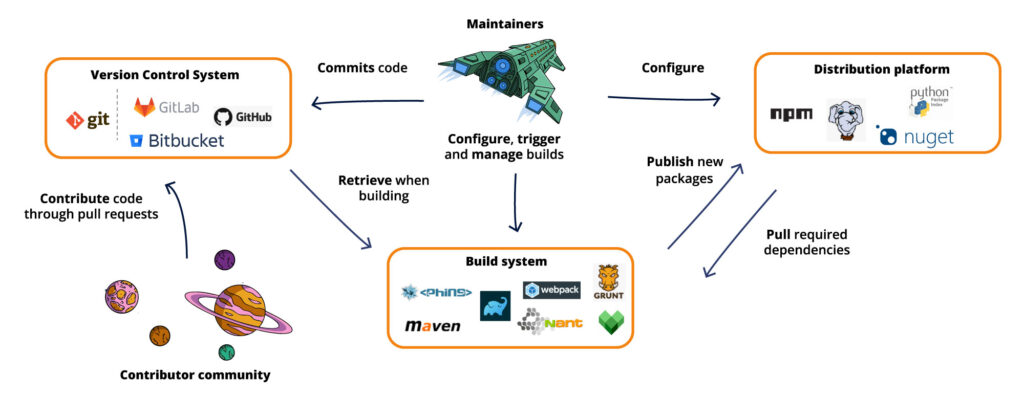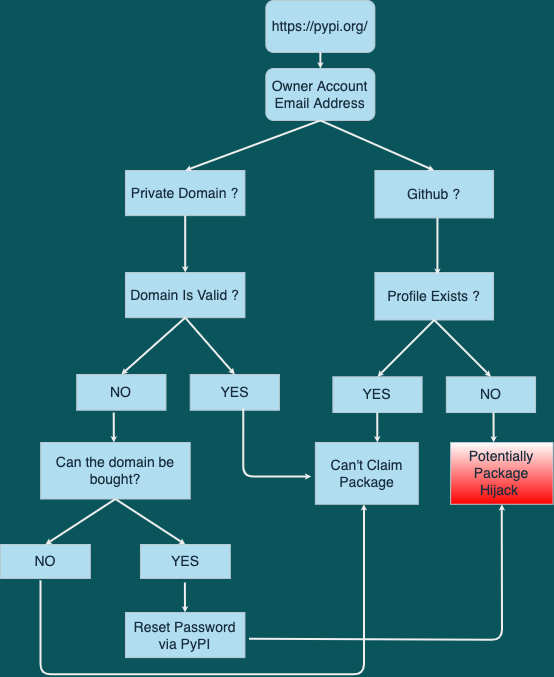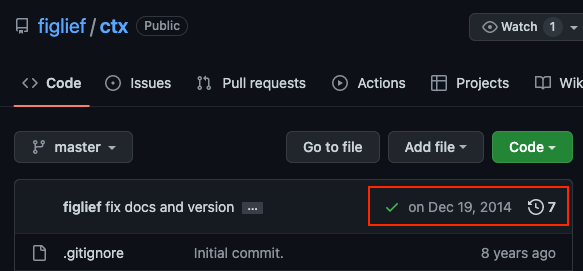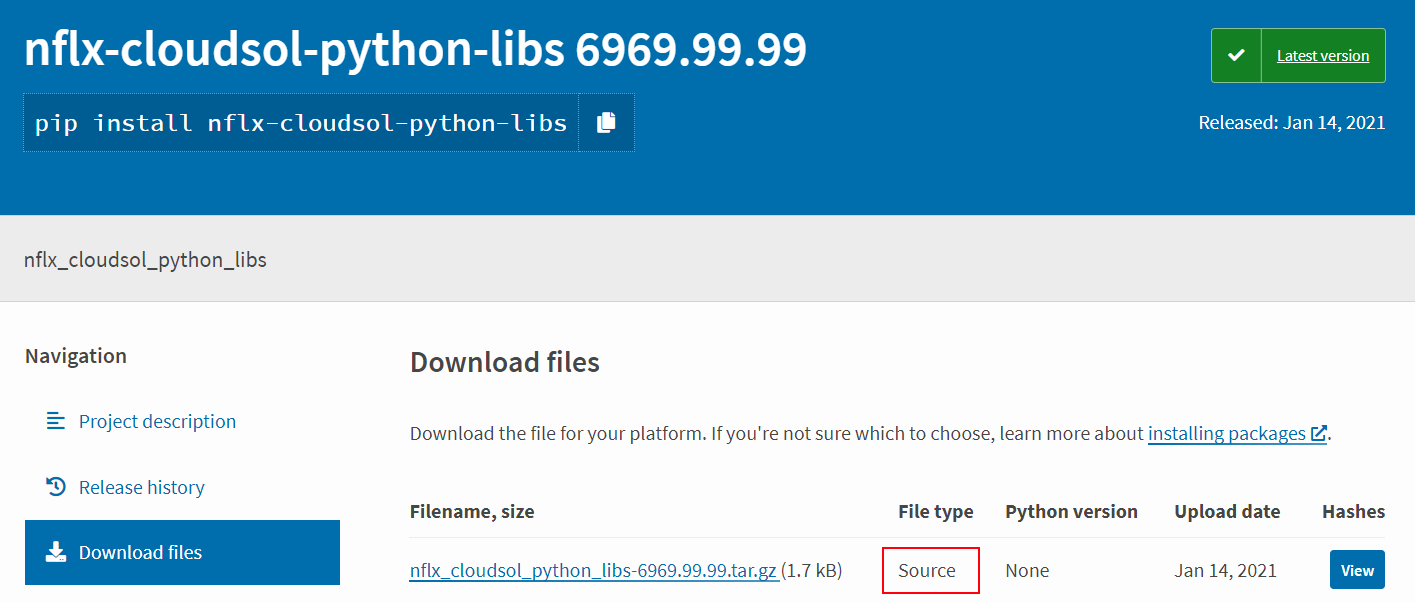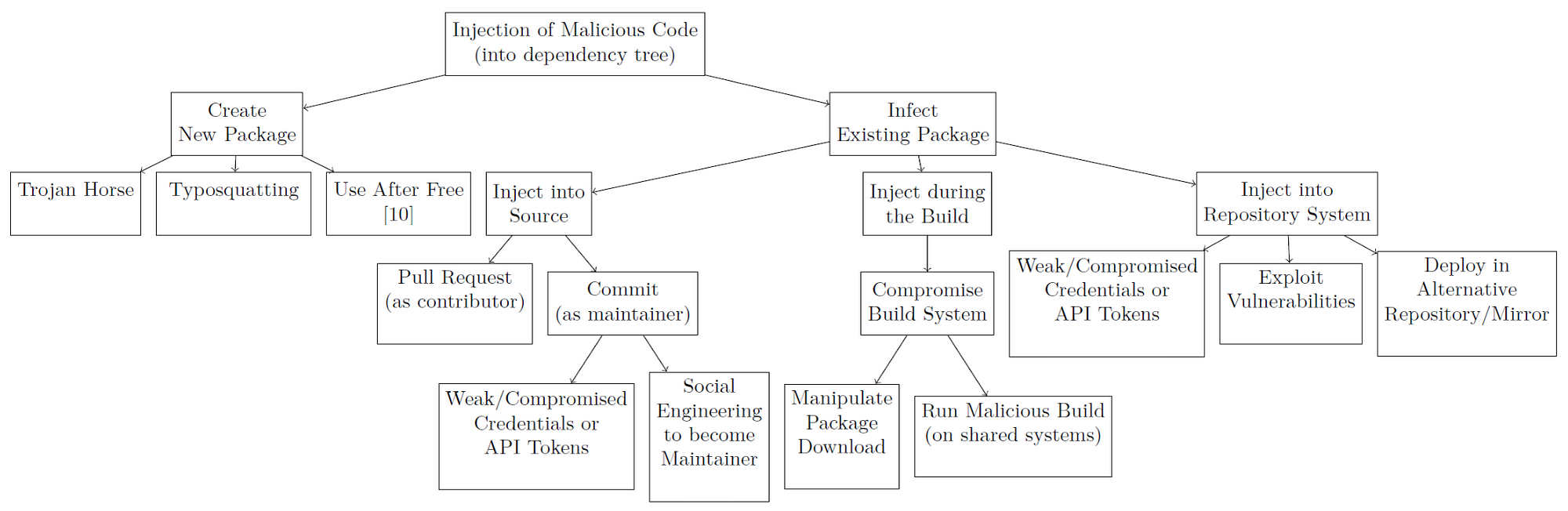
Dependency Confusion: How I Hacked Into Apple, Microsoft and Dozens of Other Companies | by Alex Birsan | Medium

Dependency confusion attack mounted via PyPi repo exposes flawed package installer behavior | The Daily Swig
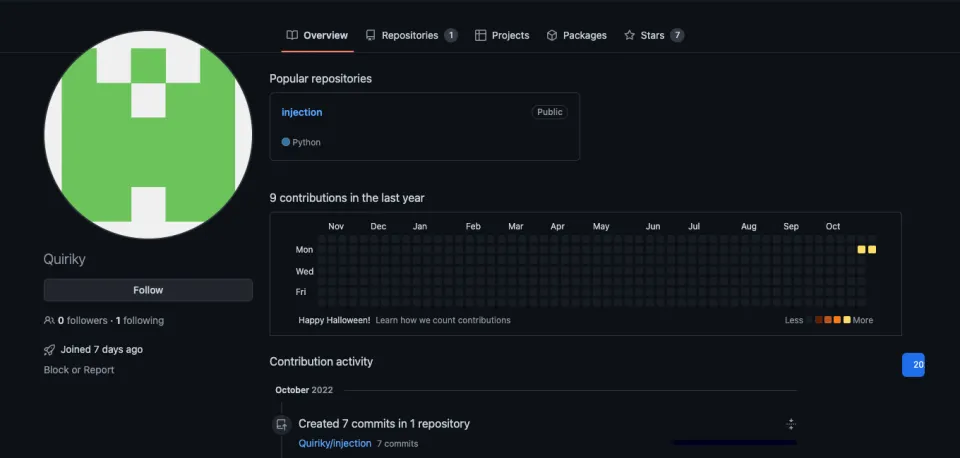
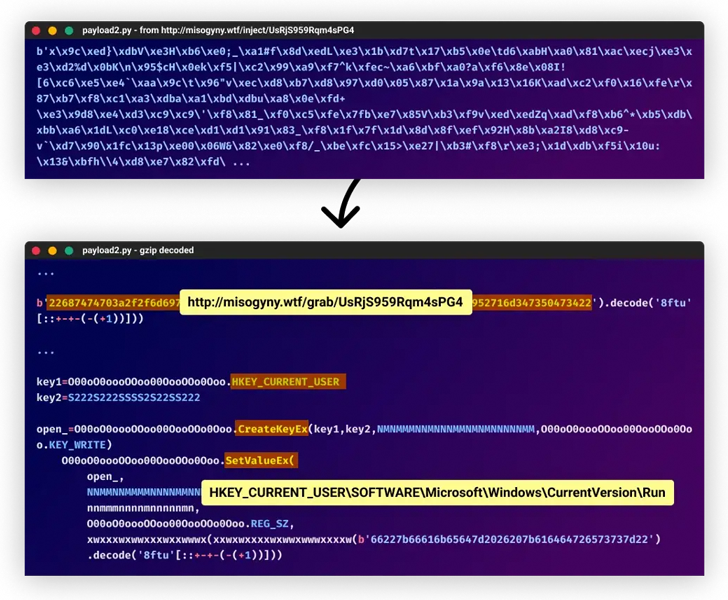
Phylum Discovers Dozens More PyPI Packages Attempting to Deliver W4SP Stealer in Ongoing Supply-Chain Attack

Python Developers are Targeted by WASP Stealer in an Ongoing Attack on Supply Chain - TrustNet Cybersecurity Solutions