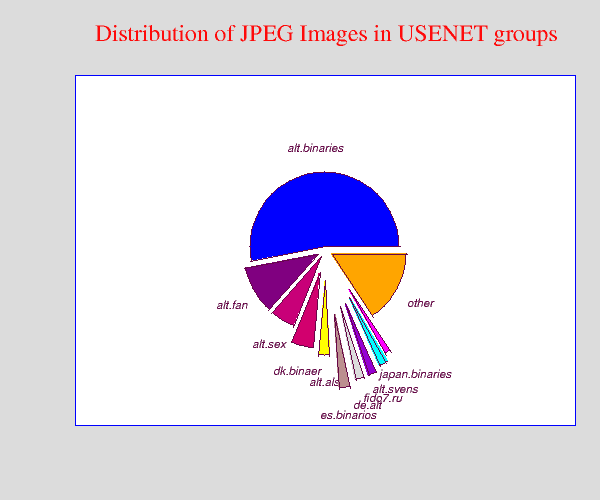
Survey on Information Assurance TEL 581 Presented by Viswesh Prabhu Subramanian Gregory Michel Lincoln Jean Louis Steganography. - ppt download

Steganography - Computer Science 1 - Assignment 5 | CPSC 1301 | Assignments Computer Science | Docsity
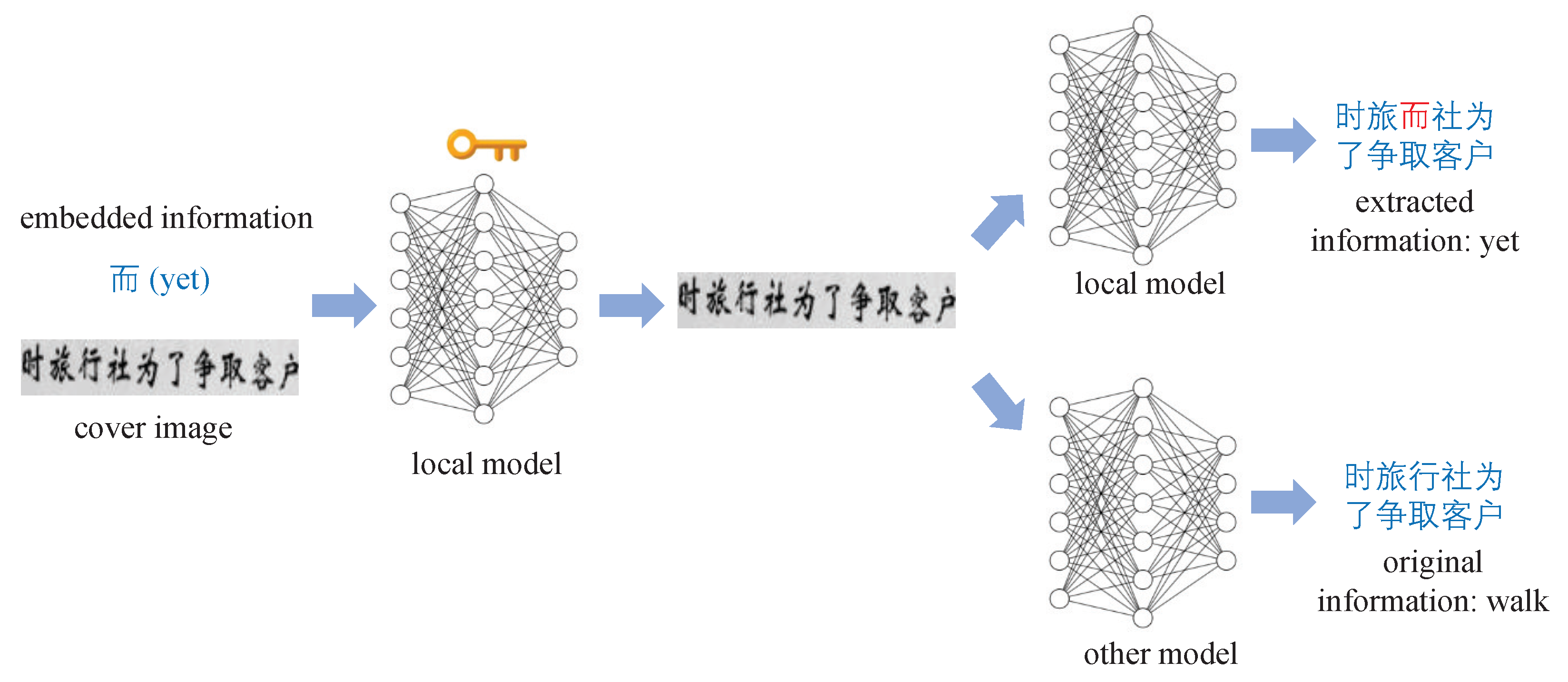
Sensors | Free Full-Text | A Novel Steganography Method for Character-Level Text Image Based on Adversarial Attacks

Sensors | Free Full-Text | A Novel Steganography-Based Pattern for Print Matter Anti-Counterfeiting by Smartphone Cameras