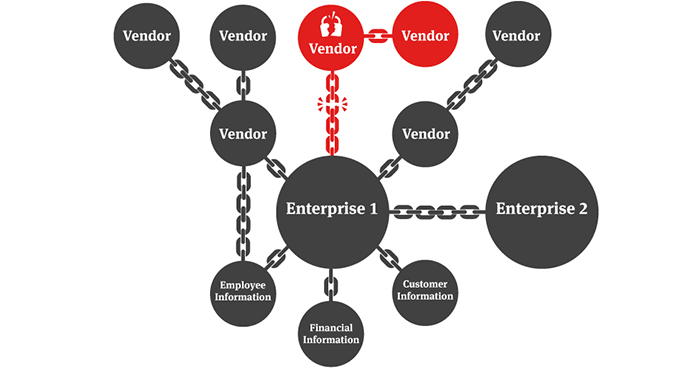
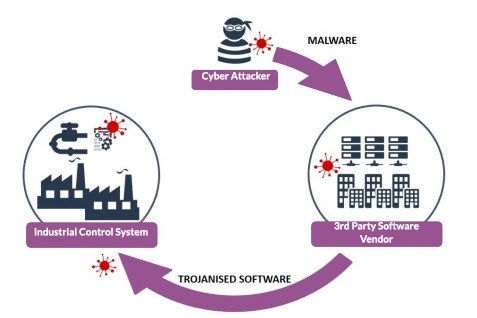
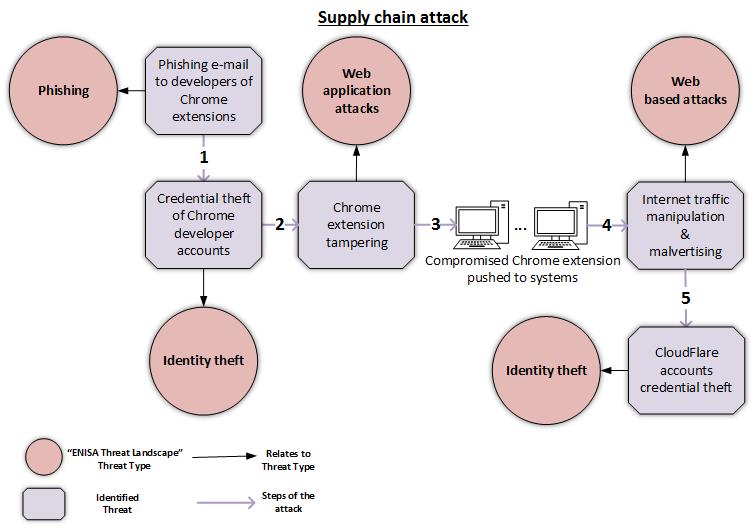
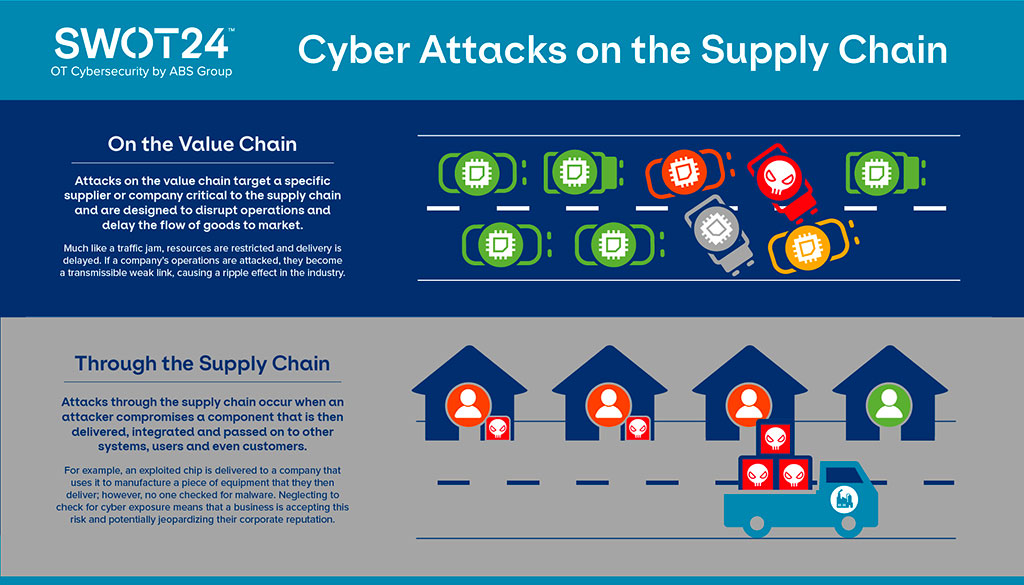
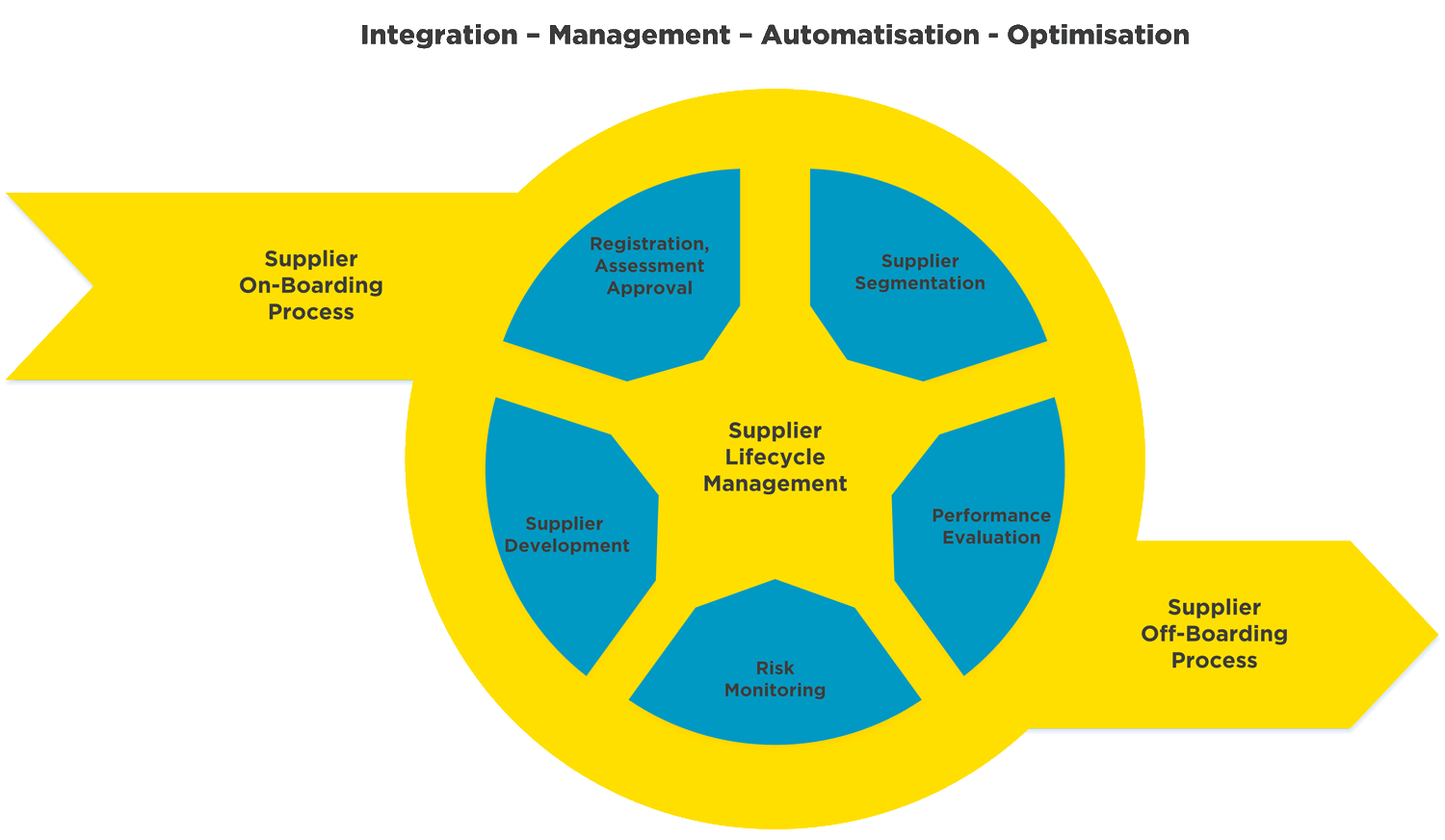
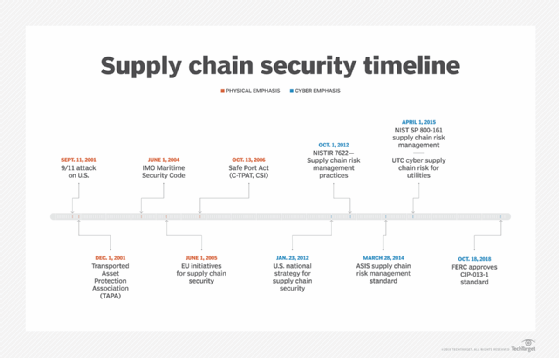
KuppingerCole - What role should Cyber Supply Chain Risk Management (#CSCRM) play in business resilience? ⛓ Considering how increasingly dependent organisations are becoming on IT services and IT support in delivering services

Understanding The Impact Cyber Threats Have On Supply Chains | Reuters Events | Supply Chain & Logistics Business Intelligence
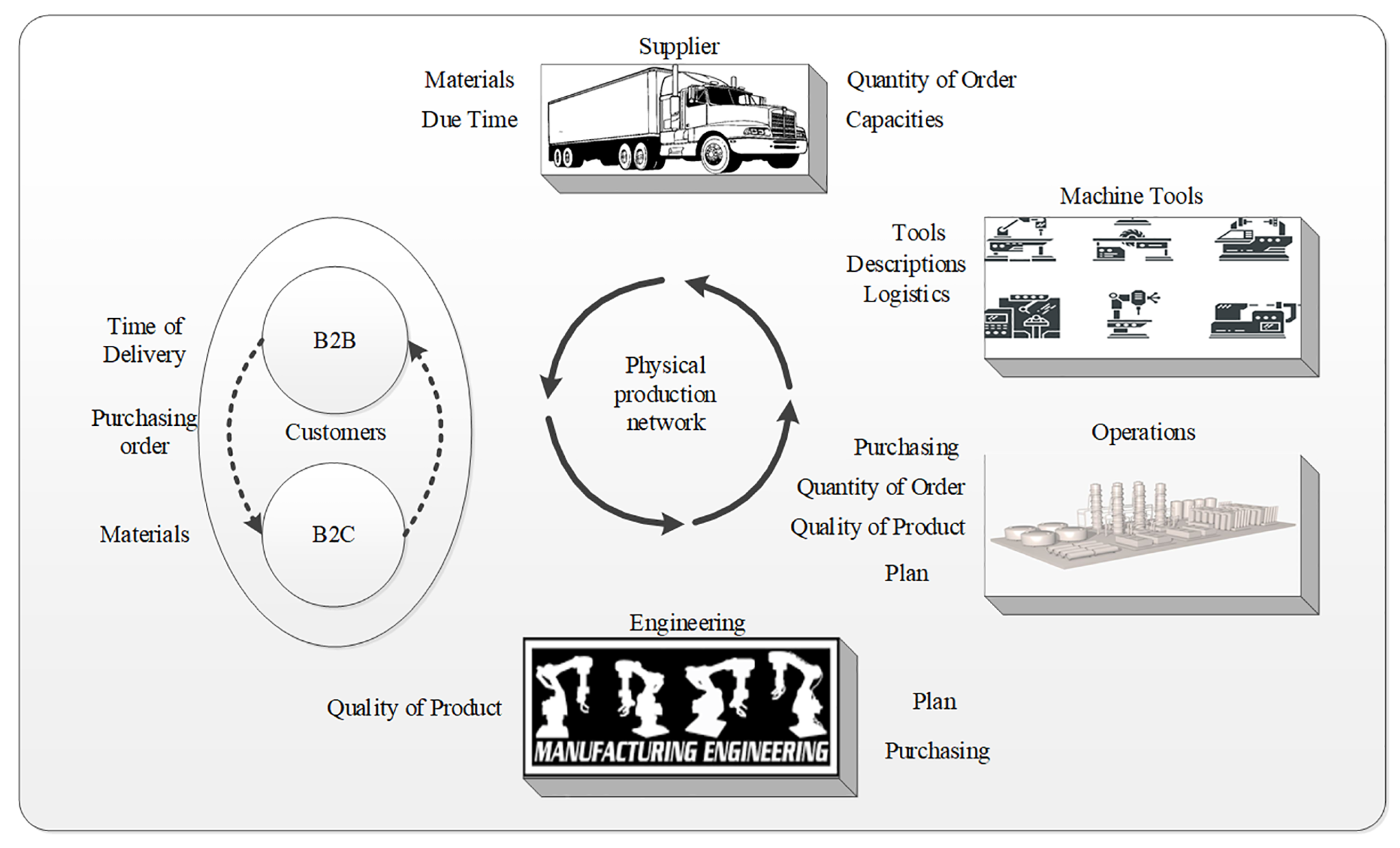
Electronics | Free Full-Text | Supply Chain 4.0: A Survey of Cyber Security Challenges, Solutions and Future Directions