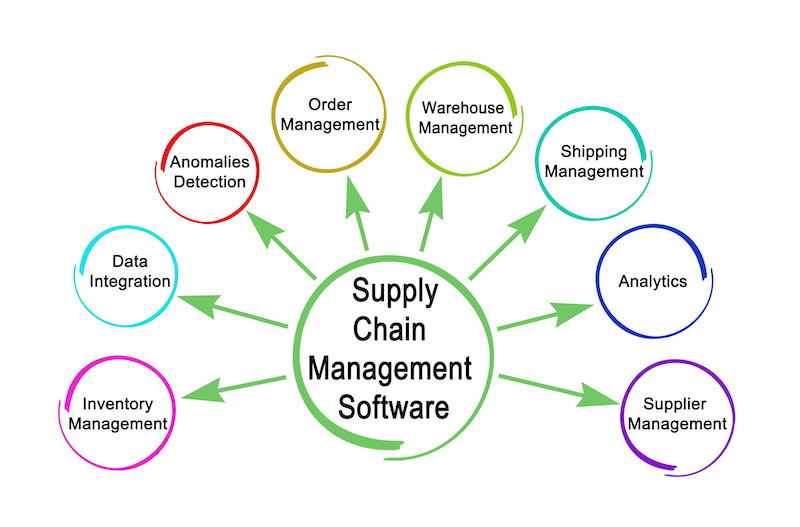
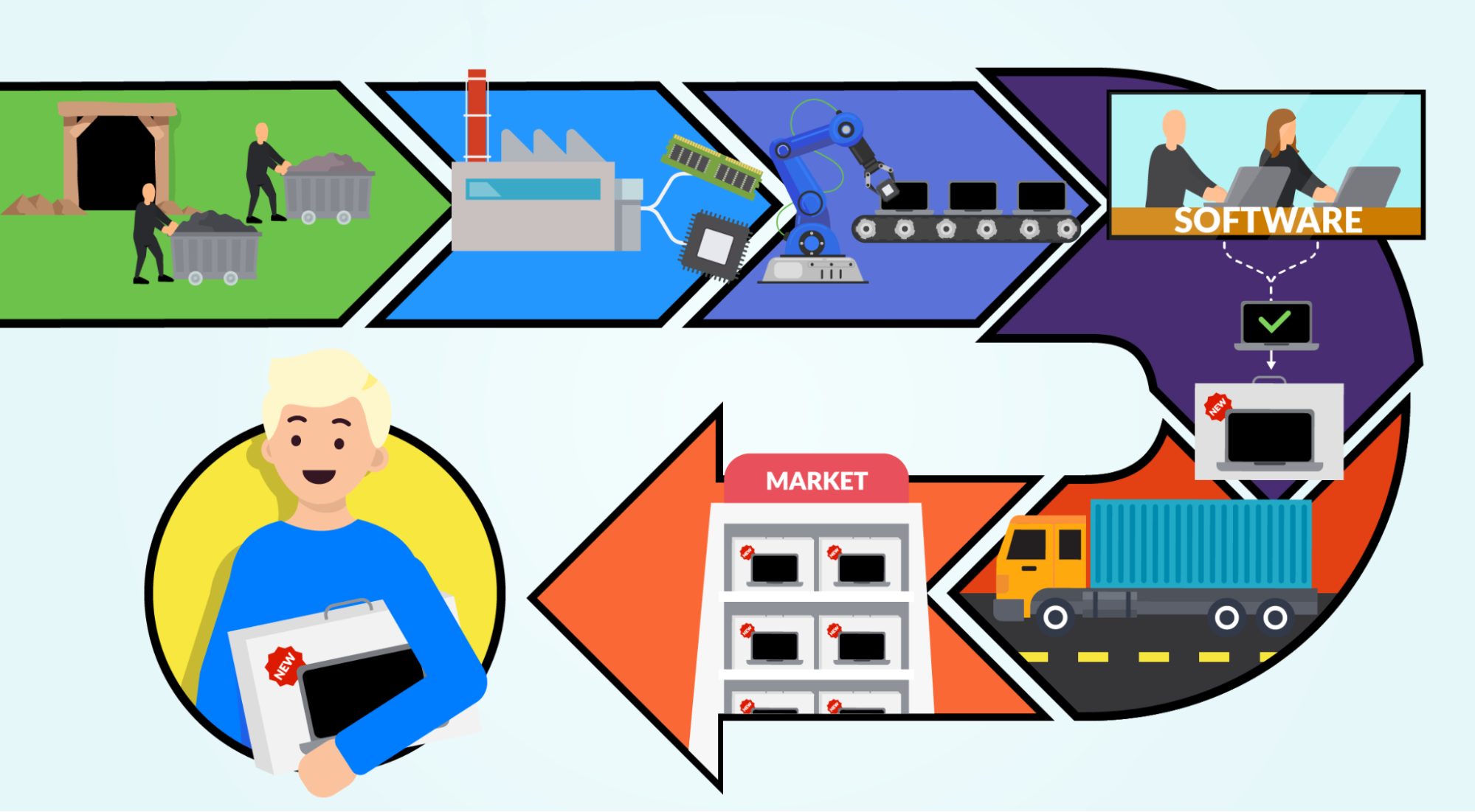
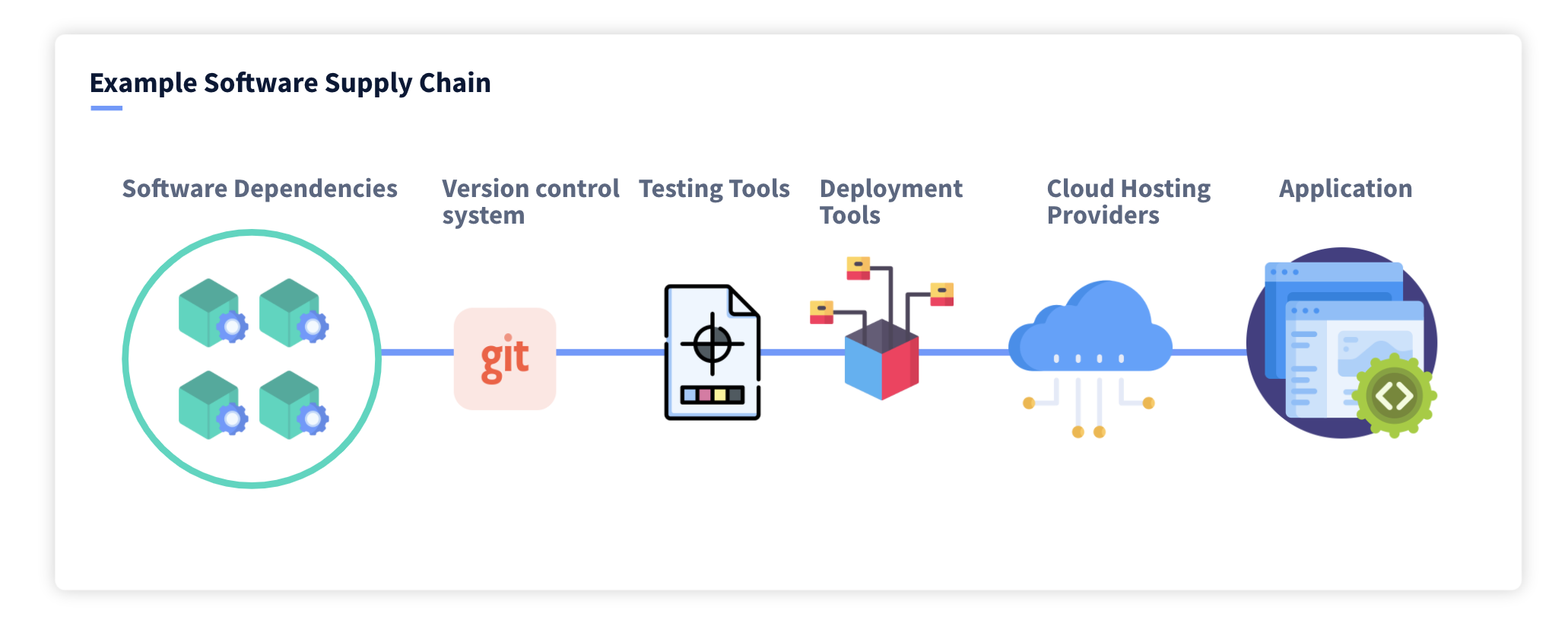
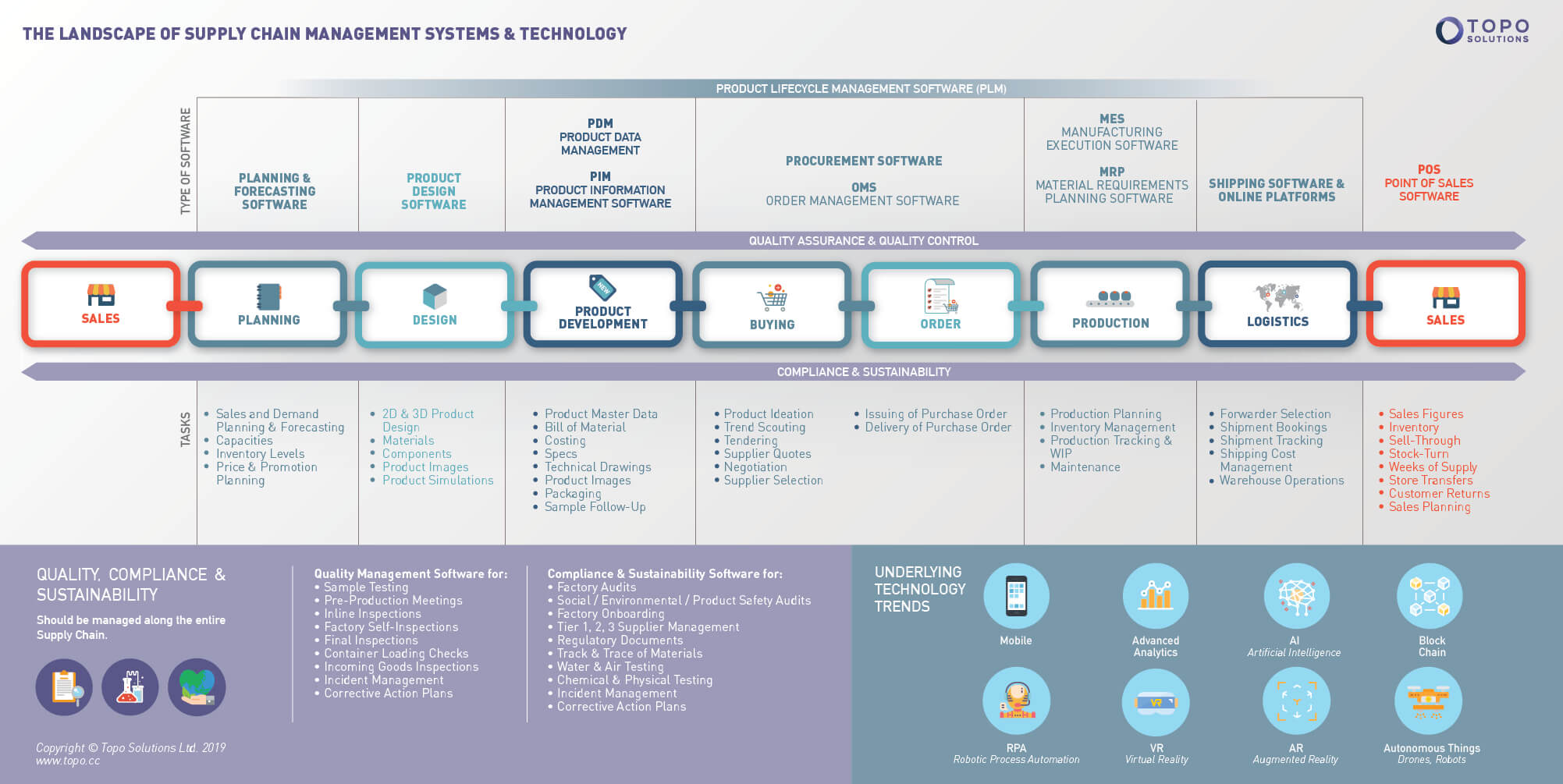
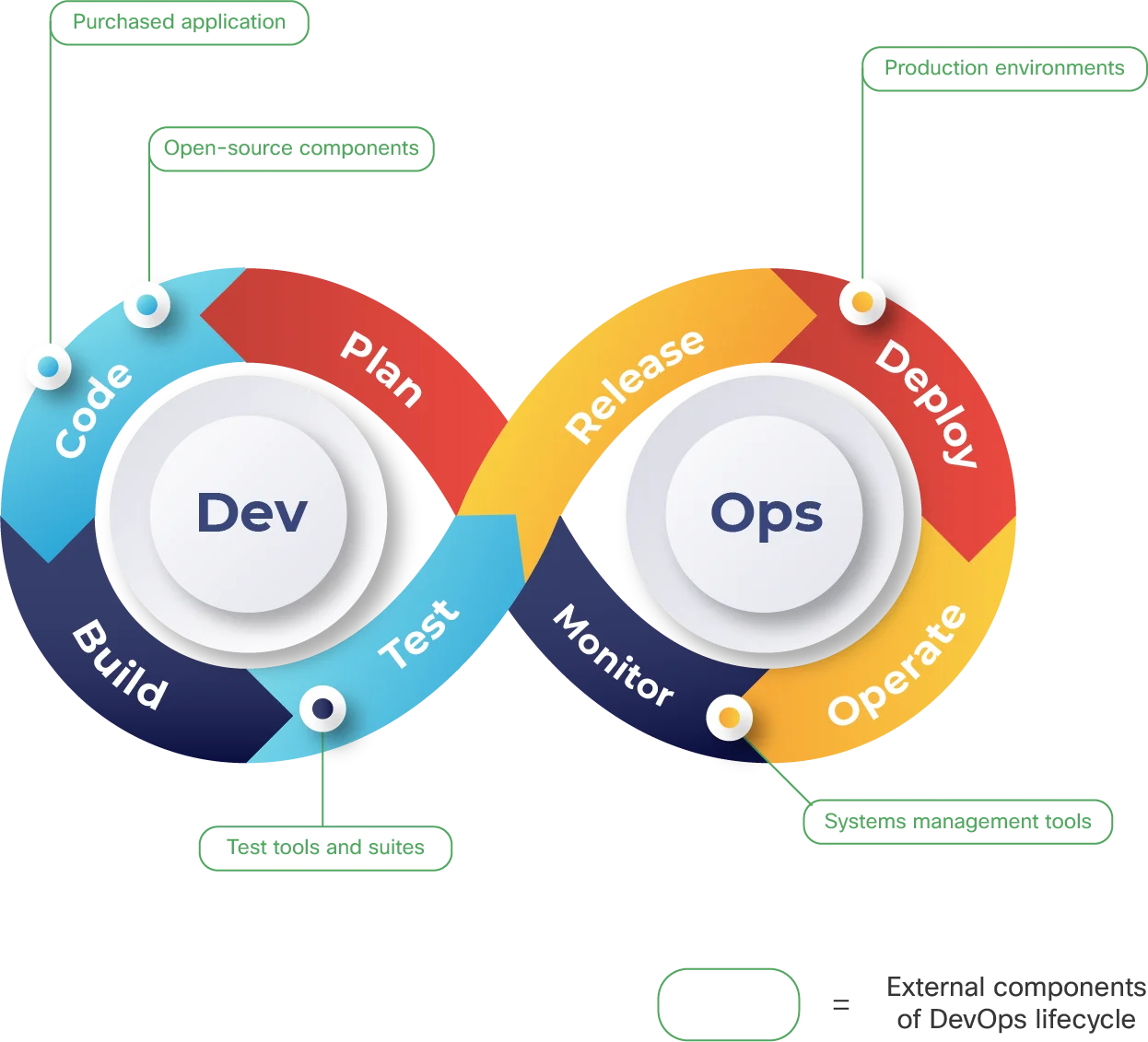
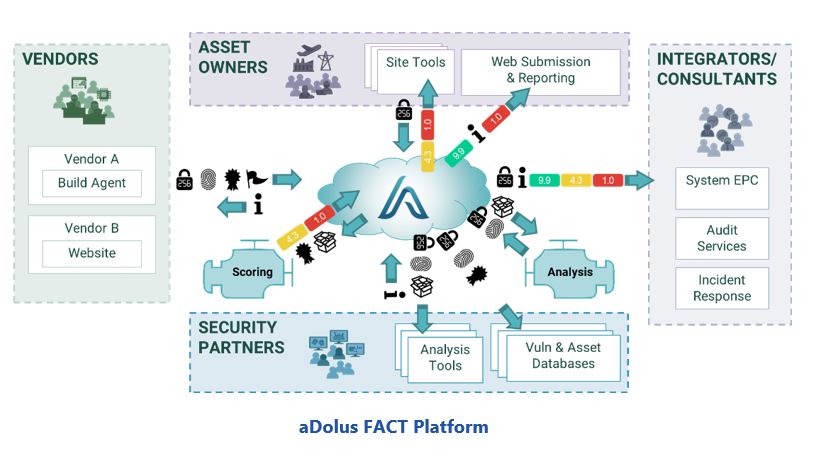
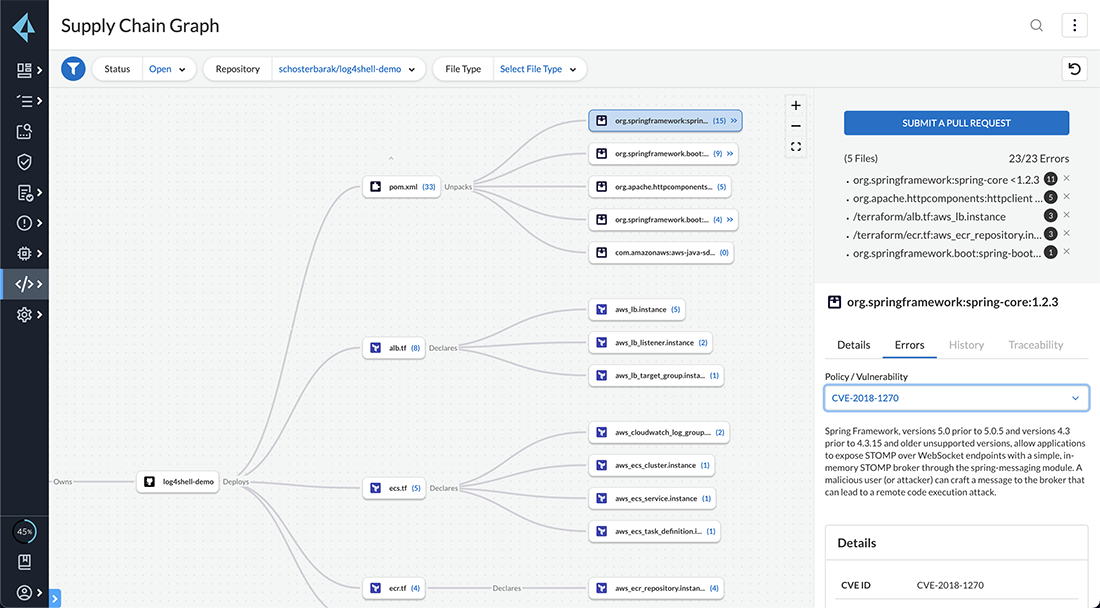
Top 15 Supply Chain Management Software in 2022 - Reviews, Features, Pricing, Comparison - PAT RESEARCH: B2B Reviews, Buying Guides & Best Practices
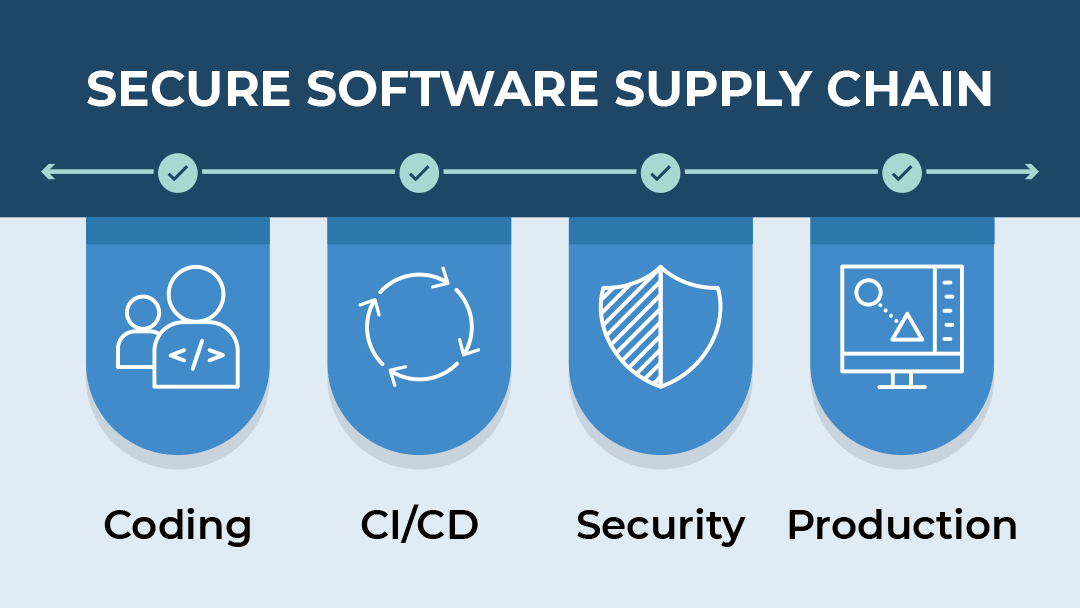
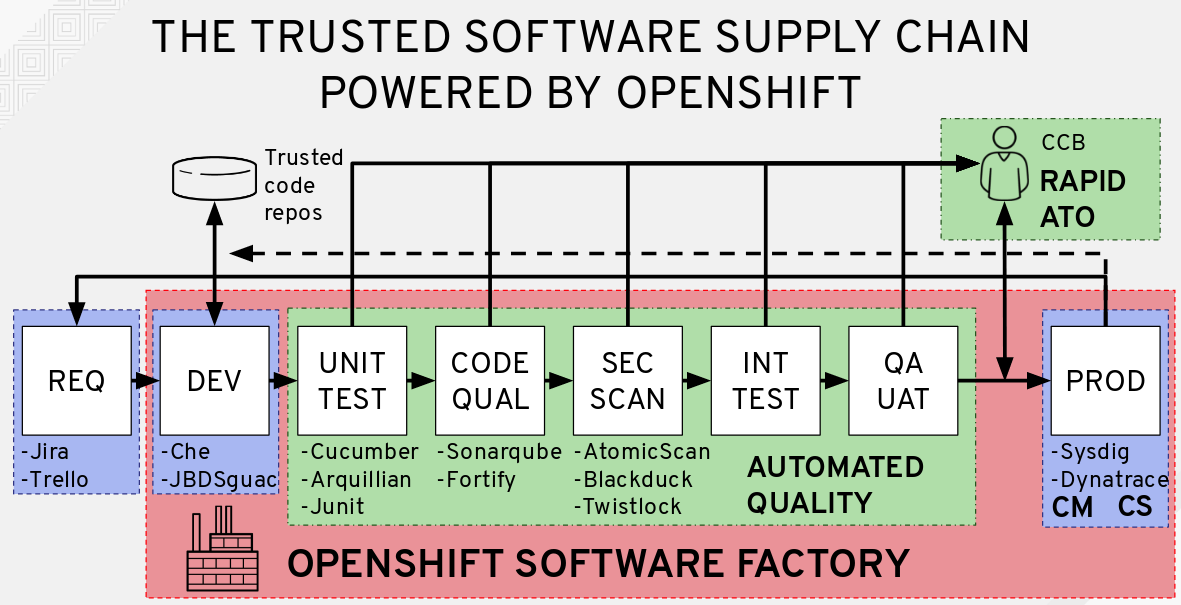
Software Supply Chain Security Ppt Powerpoint Presentation Inspiration Tips Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates